Hello,
I have a service provider that will be sending calls (INVITE) to my FreePBX but they don’t know the source IP they will sending their calls from.
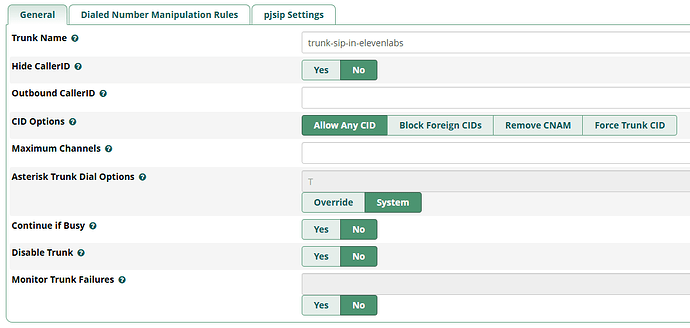
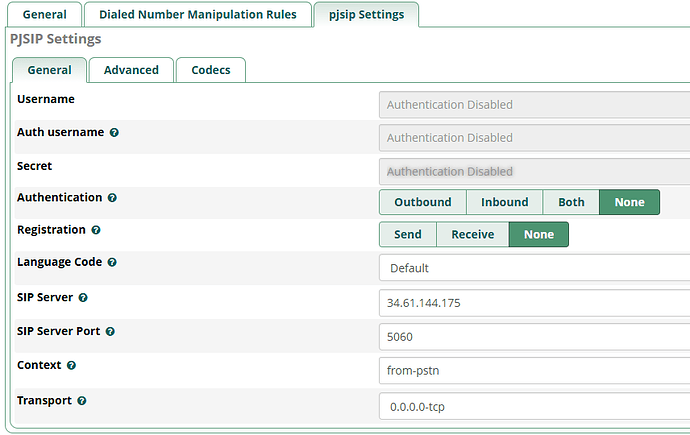
Initially i created a PJSIP trunk and added the first IP i captured from them in the SIP Server of the trunk, then i started receving the following error:
[2025-12-10 18:30:14] NOTICE[19805]: res_pjsip/pjsip_distributor.c:670 log_failed_request: Request ‘INVITE’ from ‘“17040000000” sip:17040000000<@34.61.xxx.>xxx’ failed for ‘34.61.xxx.xxx:55976’ (callid: XntbvYIVex1Huu59WYFXsrAnltJ) - No matching endpoint found after 5 tries in 0.245 ms
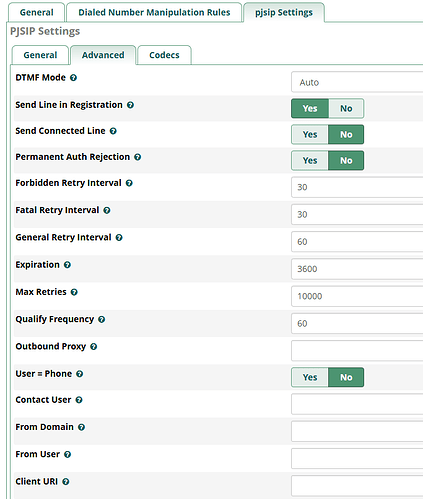
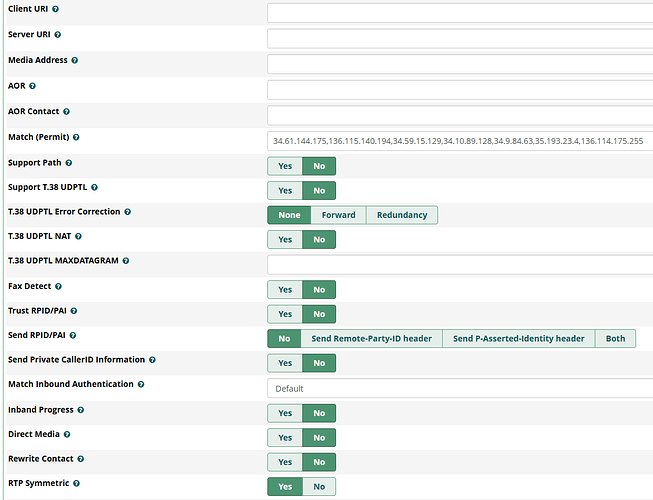
I noticed the IP was different and added both to the Match (Permit) field in the Advanced Settings and everything was fine until a new IP showed up and the same error “No matching endpoint found” was recorded.
So far i have added 7 IPs but the this service provider is so bad that they cannot answer the question of which are the possible IPs that they can send the calls from and they range they have given doesn’t match any of the 7 IPs i have seen so far.
So my question is: is there a way to create a trunk that will accept the INVITE from any IP but i will be able to match it to an endpoint so the call will get in and then i can do my magic on using the Inbound Routes and Custom Destinations as i have implemented?
BTW, the “To” header will be a fixed number potential values, so i’m hoping i can configure the trunk based on that. In the example below that would be the value “+16460000000“
Here is a snipet of the SIP conversation:
<— Received SIP request (1208 bytes) from TCP:34.61.xxx.xxx:55976 —>
INVITE ``sip:[email protected]``;transport=tcp SIP/2.0
Via: SIP/2.0/TCP 34.61.xxx.xxx:55976;branch=z9hG4bK.qTa9Rf8fCAVepfdz;alias
CSeq: 5 INVITE
Call-ID: XntbvYIVex1Huu59WYFXsrAnltJ
Content-Length: 288
To: <sip:[email protected];transport=tcp>
From: “17040000000” <sip:[email protected]:5060;transport=tcp>;tag=SCL_Z9zesLNZY7US
Contact: <sip:34.61.xxx.xxx:5060;transport=tcp>
Content-Type: application/sdp
Allow: INVITE, ACK, CANCEL, BYE, NOTIFY, REFER, MESSAGE, OPTIONS, INFO, SUBSCRIBE
Authorization: Digest username=“xxxx”, realm=“asterisk”, nonce=“1765409414/1d7943dd0b5421cdc89a800164e41e86”, ``uri="sip:[email protected]``", algorithm=md5, cnonce=“4d350260d00d7f50”, opaque=“06fe2e8d632bfc11”, qop=auth, nc=00000001, response=“b40e1369e691e54e7efaf44677a2870b”
X-Caller-ID: 17030000000
X-Conversation-ID: conv_6601kc59k46keq79vc143n0wmdmp
Max-Forwards: 70
Please let me know if this is possible.
Thanks
Camilo