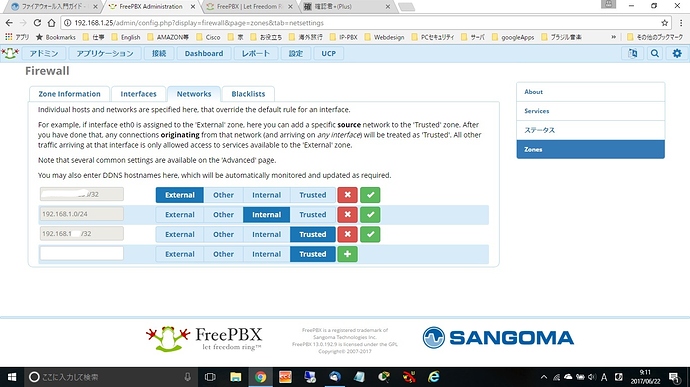
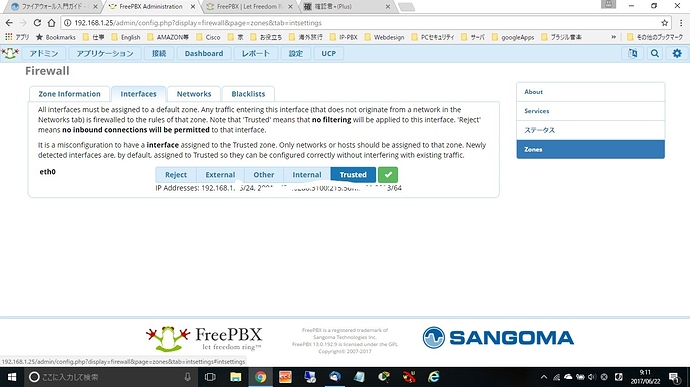
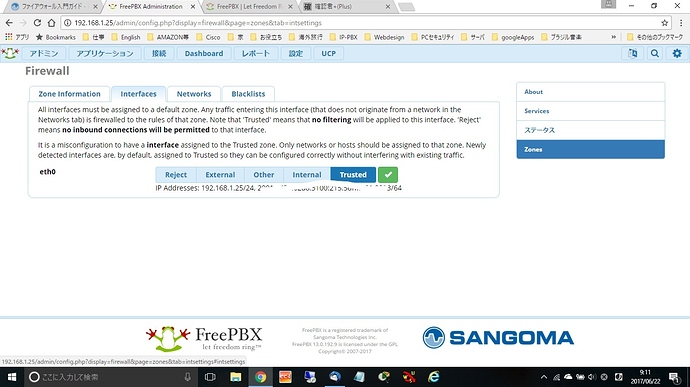
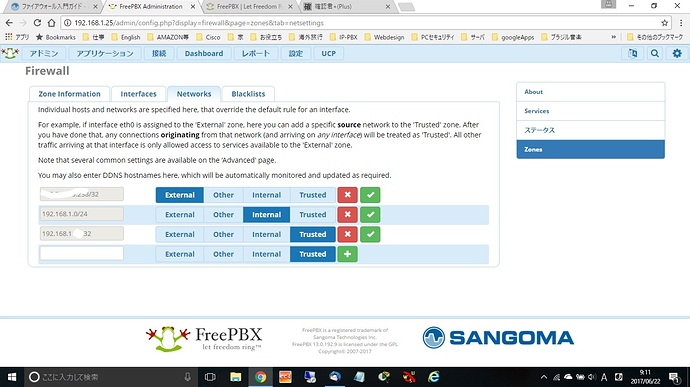
I will add the following things.
/etc/rc.d/init.d/iptables status
(abridgement)
Chain fpbxhosts (1 references)
num target prot opt source destination
1 zone-trusted all – 127.0.0.1 0.0.0.0/0
Chain fpbxinterfaces (1 references)
num target prot opt source destination
1 zone-trusted all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxknownreg (0 references)
num target prot opt source destination
1 ACCEPT all – 0.0.0.0/0 0.0.0.0/0 mark match 0x1/0x1
2 fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
3 fpbxsvc-zulu all – 0.0.0.0/0 0.0.0.0/0
4 fpbxsvc-restapps all – 0.0.0.0/0 0.0.0.0/0
5 fpbxsvc-restapps_ssl all – 0.0.0.0/0 0.0.0.0/0
6 fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
7 fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxlogdrop (1 references)
num target prot opt source destination
1 REJECT all – 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain fpbxnets (1 references)
num target prot opt source destination
1 zone-external all – .***.***. 0.0.0.0/0
2 zone-trusted all – 192.168.1.27 0.0.0.0/0
3 zone-internal all – 192.168.1.0/24 0.0.0.0/0
Chain fpbxregistrations (1 references)
num target prot opt source destination
Chain fpbxreject (1 references)
num target prot opt source destination
1 rejsvc-webrtc all – 0.0.0.0/0 0.0.0.0/0
2 rejsvc-nfs all – 0.0.0.0/0 0.0.0.0/0
3 rejsvc-smb all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxrfw (1 references)
num target prot opt source destination
1 all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: REPEAT side: source
2 all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: DISCOVERED side: source
3 fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 10 hit_count: 50 name: REPEAT side: source
4 fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 1 name: ATTACKER side: source
5 fpbxshortblock all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 60 hit_count: 10 name: SIGNALLING side: source
6 all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: SIGNALLING side: source
7 fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 100 name: REPEAT side: source
8 ACCEPT all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxshortblock (1 references)
num target prot opt source destination
1 all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: CLAMPED side: source
2 LOG all – 0.0.0.0/0 0.0.0.0/0 LOG flags 0 level 4 prefix `clamped: '
3 REJECT all – 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain fpbxsignalling (1 references)
num target prot opt source destination
1 MARK udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5160 MARK set 0x1
2 MARK udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5060 MARK set 0x1
Chain fpbxsmarthosts (1 references)
num target prot opt source destination
Chain fpbxsvc-chansip (1 references)
num target prot opt source destination
1 ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5160
Chain fpbxsvc-ftp (1 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:21
Chain fpbxsvc-http (1 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain fpbxsvc-https (1 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:443
Chain fpbxsvc-iax (1 references)
num target prot opt source destination
1 ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:4569
Chain fpbxsvc-isymphony (1 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:58080
2 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:55050
Chain fpbxsvc-nfs (0 references)
num target prot opt source destination
Chain fpbxsvc-pjsip (2 references)
num target prot opt source destination
1 ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5060
Chain fpbxsvc-provis (3 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:84
Chain fpbxsvc-provis_ssl (3 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:1443
Chain fpbxsvc-restapps (2 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:82
Chain fpbxsvc-restapps_ssl (2 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:3443
Chain fpbxsvc-smb (0 references)
num target prot opt source destination
Chain fpbxsvc-ssh (1 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain fpbxsvc-tftp (1 references)
num target prot opt source destination
1 ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:69
Chain fpbxsvc-ucp (4 references)
num target prot opt source destination
Chain fpbxsvc-vpn (3 references)
num target prot opt source destination
1 ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
Chain fpbxsvc-webrtc (0 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:8088
2 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:8089
Chain fpbxsvc-xmpp (3 references)
num target prot opt source destination
1 ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:5222
Chain fpbxsvc-zulu (2 references)
num target prot opt source destination
Chain rejsvc-nfs (1 references)
num target prot opt source destination
Chain rejsvc-smb (1 references)
num target prot opt source destination
Chain rejsvc-webrtc (1 references)
num target prot opt source destination
1 REJECT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:8088 reject-with icmp-port-unreachable
2 REJECT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:8089 reject-with icmp-port-unreachable
Chain zone-external (1 references)
num target prot opt source destination
1 fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
2 fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
3 fpbxsvc-xmpp all – 0.0.0.0/0 0.0.0.0/0
Chain zone-internal (1 references)
num target prot opt source destination
1 fpbxsvc-ssh all – 0.0.0.0/0 0.0.0.0/0
2 fpbxsvc-http all – 0.0.0.0/0 0.0.0.0/0
3 fpbxsvc-https all – 0.0.0.0/0 0.0.0.0/0
4 fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
5 fpbxsvc-pjsip all – 0.0.0.0/0 0.0.0.0/0
6 fpbxsvc-chansip all – 0.0.0.0/0 0.0.0.0/0
7 fpbxsvc-iax all – 0.0.0.0/0 0.0.0.0/0
8 fpbxsvc-zulu all – 0.0.0.0/0 0.0.0.0/0
9 fpbxsvc-isymphony all – 0.0.0.0/0 0.0.0.0/0
10 fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
11 fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
12 fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
13 fpbxsvc-restapps all – 0.0.0.0/0 0.0.0.0/0
14 fpbxsvc-restapps_ssl all – 0.0.0.0/0 0.0.0.0/0
15 fpbxsvc-xmpp all – 0.0.0.0/0 0.0.0.0/0
16 fpbxsvc-ftp all – 0.0.0.0/0 0.0.0.0/0
17 fpbxsvc-tftp all – 0.0.0.0/0 0.0.0.0/0
Chain zone-other (0 references)
num target prot opt source destination
1 fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
2 fpbxsvc-pjsip all – 0.0.0.0/0 0.0.0.0/0
3 fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
4 fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
5 fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
6 fpbxsvc-xmpp all – 0.0.0.0/0 0.0.0.0/0
Chain zone-trusted (3 references)
num target prot opt source destination
1 ACCEPT all – 0.0.0.0/0 0.0.0.0/0
[root@localhost ~]#