Hello,
I’m brand new in FreePBX.
And I need an advise from the experts.
I have the next setup: FreePBX (v.13) server behind a pfsense firewall, and another one FreePBX server on the other location.
On the pfsense I have an
OpenVPN server up and running (and a CA of course).
How I can interconnect (trunked) the two PBX servers via tunel network?
Search the forum for “pfsense” (search icon at the top right of the screen). There are several results in the top page of returned articles that should help you, especially in the VPN between servers area.
Thanks for your replay.
But my actual question was - If I have an OpenPVN server on the pfsense - what kind of setup should be done on the pfsense openVPN server (I suppese it should be site to site)? Afr\ter that what kind of export should I do (viskosity or something else)? And what should be done on the FreePBX site (that one which is not behind the pfsense)? Will it be enough if I start OpenVPN client on the freePBX server?
I will describe my rig again - I have a FreePBX server behind a pfsense firewall and 3 more FreePBX servers which are somewere in the internet. All 3 server are able to ping the world address of the pfsese (because the ICMP is still permited  ). I tried to install windows soft phones on the all 3 locations. On the Win machines I start successfuly OpenVPN clients with certificates and password protection. All 3 clients are able to call to the phones at the main locaton (which is where the initial FreePBX server located, behind the pfsense firewall). But now the requirement have been changed and they are - all locations (4 already) to have their own FreePBX server. Because of this I have to set a SIP trunks between all 4 FreePBX servers. But of course before SIP setup I heve to established a tunels between 3 freePBX servers and the pfsense.
). I tried to install windows soft phones on the all 3 locations. On the Win machines I start successfuly OpenVPN clients with certificates and password protection. All 3 clients are able to call to the phones at the main locaton (which is where the initial FreePBX server located, behind the pfsense firewall). But now the requirement have been changed and they are - all locations (4 already) to have their own FreePBX server. Because of this I have to set a SIP trunks between all 4 FreePBX servers. But of course before SIP setup I heve to established a tunels between 3 freePBX servers and the pfsense.
So if somebody have any experience with this - please help me.
BTW - in the search - I couldn’t found anything similar to what I am looking for.
Anybody? Any sugestions? Any advises? Any help? 


@hmaznev
I have used 2 PBX server different location and connected between each other via PfSense IPSec VPN tunnel.
I have this setup but with site-to-site IPSEC. In all my setups, I use OpenVPN for mobile clients and IPSEC for site-to-site.
Thats o.k. So how you do it? As I explained above one of my PBX server is behind the pfsense and the other one is … let say on an “open space”  … it is connected directly to the internet without pfsense in front of it. And my question is - what is the best client export I have to do (Inline Configurations, Bundled Configurations, Current Windows Installer, Old Windows Installers or Viscosity). Will it be enough if on the PBX server, which is on the “open space” I just start the open vpn client (like “sudo openvpn xxxx.ovpn”) and what “Server mode” on the pfsense I have to use /peer to peer (ssl/tls), peer to peer (shared key), remote access (ssl/tls), remote access user authentication or remote access(ssl/tls + user auth)/?
… it is connected directly to the internet without pfsense in front of it. And my question is - what is the best client export I have to do (Inline Configurations, Bundled Configurations, Current Windows Installer, Old Windows Installers or Viscosity). Will it be enough if on the PBX server, which is on the “open space” I just start the open vpn client (like “sudo openvpn xxxx.ovpn”) and what “Server mode” on the pfsense I have to use /peer to peer (ssl/tls), peer to peer (shared key), remote access (ssl/tls), remote access user authentication or remote access(ssl/tls + user auth)/?
Thats great, any short “How to” will be extremely helpfull to me 
Is there any reason why you have the other FreePBX directly connected to internet?
If there is no specific reason, if I were you I would also put that FreePBX behind a pfSense device and establish a site-to-site IPSEC.
If there is a specific reason why FreePBX must be connected directly to internet, then create the OpenVPN server on pfSense and then export the client configuration using the button that says “Most clients” under “inline configurations”. That will result in a single file with all the info and certificates inside that one file.
Keep in mind that the PBX1 and pfsense are in one network, let say 192.168.10.0 which is gointg out via GW (the world addess of the pfsense) 10.10.10.2. the other PBX is in the network 192.168.20.0 which is going ot to the internet via GW 10.10.10.1.
Ohhh … yes there is a specific reason the second PBX to be connected directly to the internet … it is long story.
o.k. I will do wta you do advise me. And still have a question - will be enough (from the asterix and freepbx point of view) if I just start the openvpn client (which is embeded in the distro) on the second pbx server like (sudo openvpn xxxxxx.ovpn)?
Can you post a network map? I don’t think I follow your setup.
In regards to starting the OpenVPN client, yes, just execute sudo openvpn --config XXXXXX.ovpn
Verify that the ovpn config file has the correct IP address or DNS hostname that belongs to the OpenVPN server.
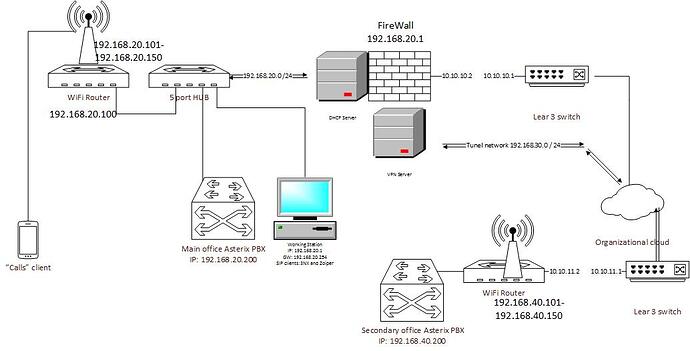
That is the simplified network diagram.
Of course it is easy to follo the setup when it is graphicali represented. Sorry it doesn’t come to my mind to post it earlier. The only thing I didn’t put in the map is that the router of at the secondary site has an internal address 192.168.40.1
I hope now it is a little bit more clear.
BTW I am able to ping from main site network the world addres of the secondary site lear 3 switch and of course from the site 2 network the world address of the pfsense.
I tried - I istalled a softphone on the client machine in the site 2 and absolutely successfuly connected it to the PBX in the main site via open VPN server at the pfsense and openVPN client started on the windows box in the internal net of the site 2. There were no problebs at all. Calls were o.k. and the voice was perfect in both directions.
But now the requirements were changed - the client wants site 2 to be independent (in case the main site is unreachible -the want to have their communications in site2.) That is why I have to put another PBX box in site 2 and to set trunk between Main PBX and the secondary PBX. And because I do not have permitions to touch the lear 3 switches - I have to establish VPN tunel between secondary PBX and the pfsense in order both PBX boxes to feel themself as they are in the one and the same network.
I’m still trying to understand. Where in that graphic would the pfsense box be? Which one is site 1 and wich one is site 2? If you have routers on both sites, you should be able to create a VPN between them in theory.
Site 1 is on the left hand site of the graphic, site2 is on the right down corner of the map. pfsense box is named “firewall” and it is almost in the up-middle part of the graph. The routers on both sites are used first at all to extend the local networks on both sites (1 and 2). We use such a setup because we are permited to use only 2 (two ) IP addresses on both sites of the organizational cloud (corporate network). So looking to site 1 (left hand site of the map) I am allowed to use 10.10.10.1 as a GW to the corporate cloud and just one IP address (10.10.10.2) for client in the site 1 local network. Because of this I put a router (in this case pfsense box) in order to extend the site 1 local network.
Similar is the situation for site 2 (down - right corner of the graph). But the administrator there doesn’t want to use pfsense box and in order to extend the site 2 local network put some … how to say … let say router for a home use :). I am not able to create VPN between pfsense and slim home router. That is why I want to set a VPN between the pfsense box and PBX box.
Which ones are your gateways to the internet? Because 10.x.x.x is a private non-routable network.
Of course Ali,
That was why I typed in the cloud that this is a corporative (organizational) cloud. I do not have a GW to the Internet. It is a corporate (internal) intranet. So axcept that the 10.10.10.1 and 10.10.11.1 are the gateways to the Internet. Everything in the corporate intranet is routable in the very same way as in the Internet.
So if this is all a private network, you shouldn’t need a VPN as all the traffic remains private. Is that right? Or is there some part of the traffic that could be traversing the public internet?
I definetely need a VPN. I do not know what to think - if I do not explain my point right, or you cannot understand me. The network is private, but on both sites of the corporate cloud I can use just ONE IP address. That is why I have pgsense box on my site and the other office has it’s router. The PBX box is behind the pfsense in my part of the network and the PBX for site 2 is behind the router. In this case the point of the VPN is not just security, but to put both PBX servers in one and the same network.