the last answer was to stop a specific user which I figured so I gave credit to solving it which may have reduced correspondance so now I want to stop the sip vicious and friendly scanner attacks…
Use a firewall, only allow trusted traffic to the PBX. Dont use 5060, 5160, etc, use a non-standard Port to Listen On.
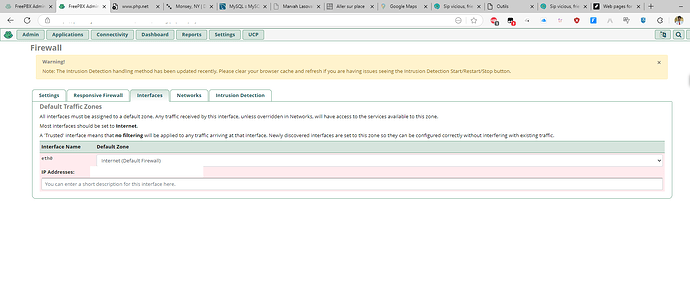
Default Traffic Zones
All interfaces must be assigned to a default zone. Any traffic received by this interface, unless overridden in Networks, will have access to the services available to this zone.
Most interfaces should be set to Internet.
A ‘Trusted’ interface means that no filtering will be applied to any traffic arriving at that interface. Newly discovered interfaces are set to this zone so they can be configured correctly without interfering with existing traffic.
| Interface Name | Default Zone |
|---|---|
| eth0 | |
| IP Addresses: | 128.140.35.99/32, 2a01:4f8:1c1c:5282::1/64 |
so I should set this to trusted correct? what does it mean?
just want to make sure we are talking about the same thing… so I change this to trusted? and what are the consequences, what does it mean?
Stepping back a bit I’ll ask this, do the calls appear in FreePBX call logs?
This refers to Sip vicious, call scanner , phone ringing all night
“Friendly scanner” isn’t an attack type, but rather what the FreePBX dialplan reports when a call arrives for an unknown DID. Where the cause of this is malicious, one can normally stop it by not enabling anonymous callers. With chan_pjsip, there should not really need to be any reason to enable these, although with chan_sip, it was sometimes necessary when a provider could originate traffic from a range of addresses. chan_pjsip, allows you to specify a list of addresses and address ranges for an endpoint.
@david55 It’s part of the SIP signaling of the calls.
I’m not sure how to get that do you mean Call event logger?
I went to /var/log/asterisk and downloaded full then I see the following some modifications made to preserve anonimity:
[2025-01-29 13:50:45] VERBOSE[65317] res_pjsip_logger.c: <— Received SIP response (405 bytes) from UDP:323232.333.2332.33:5060 —>
SIP/2.0 200 Keepalive
Via: SIP/2.0/UDP 99.233.233.32:15060;rport=15060;branch=z9sdfdsf3a2-dsfsdfdsffds;received=99.233.233.32
From: sip:[email protected];tag=fdasfsdfsdsdf6
To: sip:[email protected];tag=6cc4260d7bb2fdfdsdfd
Call-ID: dsfsdfsdfsddfs
CSeq: 26550 OPTIONS
Content-Length: 0111
That’s not a call or anything. Asterisk sent a SIP OPTIONS request to something remote, and it responded successfully.
In FreePBX I believe they’re just called CDR, where it is I don’t know.
Why I’m asking is that it is possible for these calls to arrive directly to a phone, without going through FreePBX, depending on the network equipment. I’ve seen threads previously where people think it is going through FreePBX but after investigation it never was - so all their attempts to resolve it there didn’t do anything. Instead it was going directly to the phone. They either changed the router, configured it differently, or some phones have the ability to limit who they accept calls from to only the server they’re expecting it from.
I have seen terrible network/firewall configurations where the phone pulls a WAN address, effectively leaving the phone open to the world to probe.
So Joshua’s theory could be correct.
“Friendly scanner” is text from the source code of FreePBX.
@david55 I’ve also seen it appear in the SIP INVITE itself too.
This topic was automatically closed 30 days after the last reply. New replies are no longer allowed.