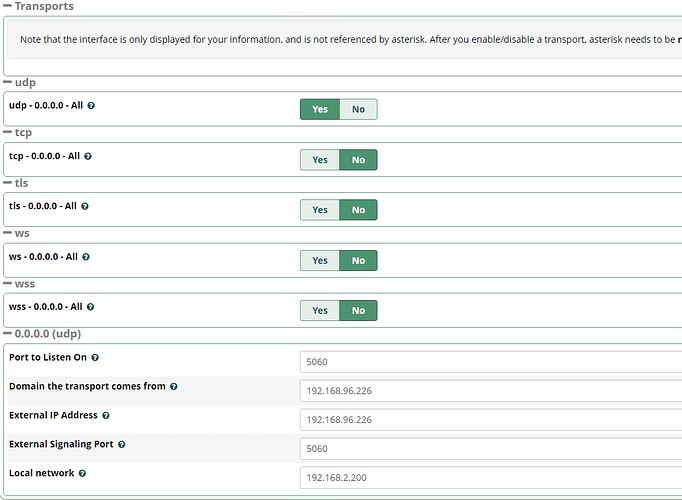
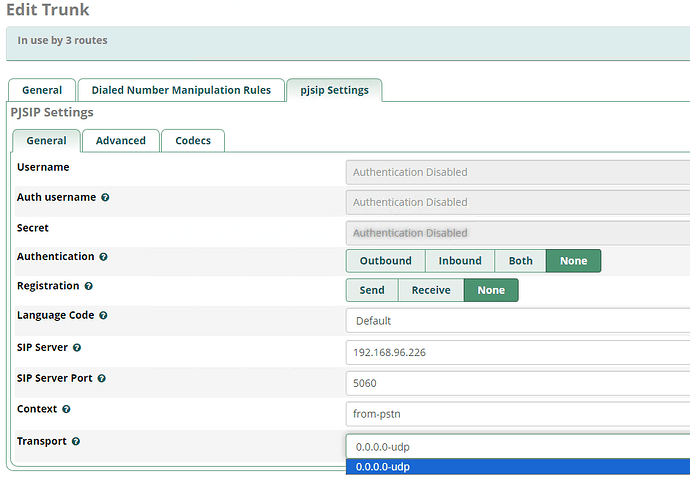
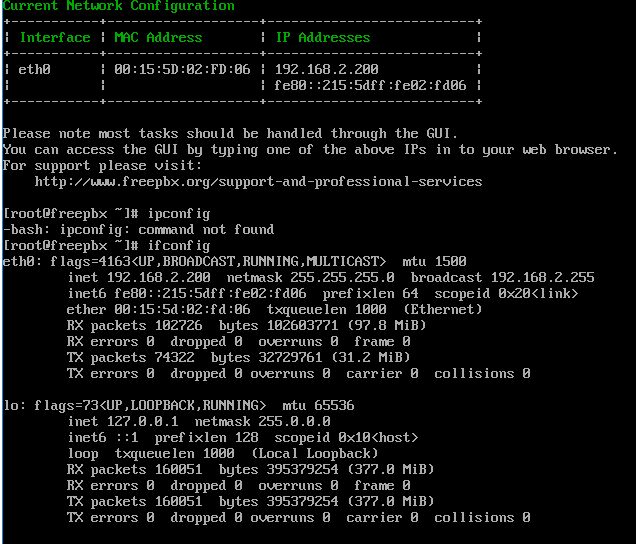
Can someone guide on how to setup trunk for the following guidelines I have the ip address and the phone number for testing. Any help would be greatly appreciated.
CODECs Supported: G.711 u-law, G.729A/B
SIP Trunk Type: Peer-to-Peer Trunk(1)
SIP RFCs Supported: 2833, 3261, 3325, 5806
SIP METHODS Unsupported: NOTIFY, REFER, SUBSCRIBE, UPDATE
SIP HEADERS Supported : From, To, PAI, RPID, Privacy, Diversion, Via, Contact, Expire
SIP OPTIONS PING Support : Supported
Recommended SIP Session Timers: In accordance with RFC 3261
Transport Protocol: UDP PORT 5060(2)
RTP Port Ranges: 16384-65535
Call Forwarding, SIM Ring, Find-me/Follow-me: In accordance with RFC 5806
Max Forwards: Set to 70
DTMF Support: RFC 2833
Default Sampling Rate : 20ms
Default Max Calls per Second Per SIP Trunk: 10
FAX Support: T.38 with G.711u fallback
Transcoding Support: No
Inbound and Outbound Calling Party Presentation: 10 digits or E.164 Format(3)
Calling Privacy Support: In accordance with RFC 3325
Calling Name Support: Provider will accept when provided but does not deliver to Terminating Carrier.
Calling Party Override Support : Yes(4)
(1) No password, user name, or authentication is necessary or required. Authentication is currently not supported.
(2) Provider does not currently support TCP protocol over SIP commonly used for Microsoft’s Skype for Business.
(3) The default inbound calling party number format from Provider is presented with 10 digits (NPANXXYYYY) - E.164 format (+1NPANXXYYYY) is also supported but must be requested. The customer is expected to send a valid Provider SIP service 10 digit or E.164 formatted calling party number.
(4) Customer may override Calling Party Number on outbound traffic in the FROM header provided PAID, RPID, and/or Diversion is populated with a valid Provider DID built on the SIP service.
Note: Diversion is not supported for international calls.
Some additional details on calling party number requirements:
For outbound calls a valid Provider SIP service number is required in at least one of the following (in order of precedence):
Diversion header
P-Asserted-Identity header (PAID)
Remote-Party-ID header (RPID)
From header
For VoIP network admission calls are screened once – looking for a diversion header first, and if present that number will be evaluated. (If the diversion header is invalid the call will likely fail.)
From there, if there is no diversion header the switch will look for PAID and evaluate that if present. (If the PAID is invalid, again the call will likely fail.)
The process will continue looking for/at RPID and From with the same evaluation.