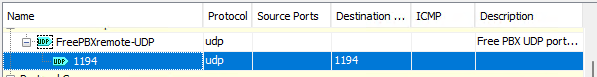
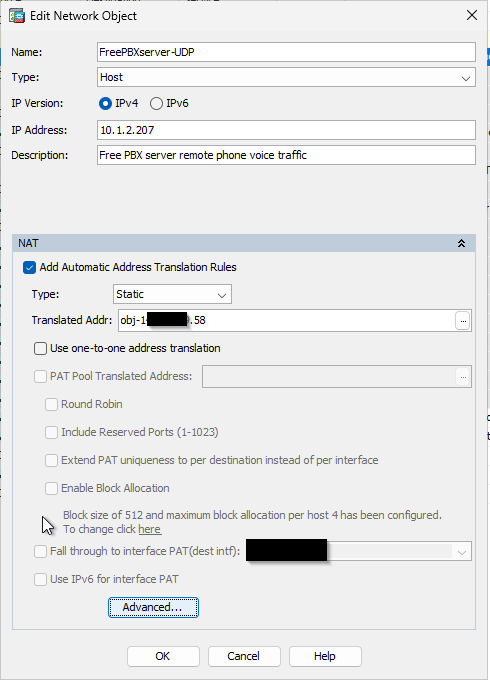
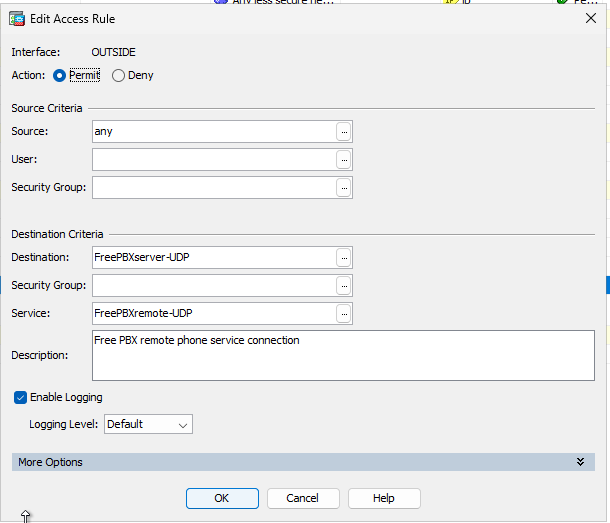
Here are the Some Log Files from the PBX Server for OpenVPN. Working and not working.
Not Working
Thu Nov 21 16:21:01 2024 174.193.112.142:8255 TLS: Initial packet from [AF_INET]174.193.112.142:8255, sid=abd57c71 91f4091c
Thu Nov 21 16:21:03 2024 174.193.112.142:8255 CRL: loaded 1 CRLs from file sysadmin_crl.pem
Thu Nov 21 16:22:01 2024 174.193.112.142:8255 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu Nov 21 16:22:01 2024 174.193.112.142:8255 TLS Error: TLS handshake failed
Thu Nov 21 16:22:01 2024 174.193.112.142:8255 SIGUSR1[soft,tls-error] received, client-instance restarting
Thu Nov 21 16:23:21 2024 174.193.112.142:8226 TLS: Initial packet from [AF_INET]174.193.112.142:8226, sid=52c7c091 00ab6ff6
Thu Nov 21 16:23:28 2024 174.193.112.142:8226 CRL: loaded 1 CRLs from file sysadmin_crl.pem
Thu Nov 21 16:24:21 2024 174.193.112.142:8226 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu Nov 21 16:24:21 2024 174.193.112.142:8226 TLS Error: TLS handshake failed
Thu Nov 21 16:24:21 2024 174.193.112.142:8226 SIGUSR1[soft,tls-error] received, client-instance restarting
Thu Nov 21 16:27:01 2024 174.193.112.142:8243 TLS: Initial packet from [AF_INET]174.193.112.142:8243, sid=034822c4 dd1fd134
Thu Nov 21 16:27:03 2024 174.193.112.142:8243 CRL: loaded 1 CRLs from file sysadmin_crl.pem
Thu Nov 21 16:28:01 2024 174.193.112.142:8243 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu Nov 21 16:28:01 2024 174.193.112.142:8243 TLS Error: TLS handshake failed
Thu Nov 21 16:28:01 2024 174.193.112.142:8243 SIGUSR1[soft,tls-error] received, client-instance restarting
Thu Nov 21 16:38:00 2024 172.58.165.225:58716 TLS: Initial packet from [AF_INET]172.58.165.225:58716, sid=e2e2ff7c e047eafb
Thu Nov 21 16:38:07 2024 172.58.165.225:58716 CRL: loaded 1 CRLs from file sysadmin_crl.pem
Thu Nov 21 16:39:01 2024 172.58.165.225:58716 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Thu Nov 21 16:39:01 2024 172.58.165.225:58716 TLS Error: TLS handshake failed
Thu Nov 21 16:39:01 2024 172.58.165.225:58716 SIGUSR1[soft,tls-error] received, client-instance restarting
Working
Thu Nov 21 17:14:22 2024 172.58.165.141:31792 TLS: Initial packet from [AF_INET]172.58.165.141:31792, sid=5eb7eb2d e54c757b
Thu Nov 21 17:14:53 2024 172.58.165.141:31792 CRL: loaded 1 CRLs from file sysadmin_crl.pem
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 VERIFY OK: depth=1, CN=FreePBX
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 VERIFY OK: depth=0, CN=client9
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_VER=2.4.9
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_PLAT=linux
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_PROTO=2
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_NCP=2
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_LZ4=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_LZ4v2=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_LZO=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_COMP_STUB=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_COMP_STUBv2=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 peer info: IV_TCPNL=1
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 WARNING: ‘link-mtu’ is used inconsistently, local=‘link-mtu 1542’, remote=‘link-mtu 1570’
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 WARNING: ‘cipher’ is used inconsistently, local=‘cipher BF-CBC’, remote=‘cipher AES-128-CBC’
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 WARNING: ‘auth’ is used inconsistently, local=‘auth SHA1’, remote=‘auth SHA256’
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Thu Nov 21 17:15:01 2024 172.58.165.141:31792 [client9] Peer Connection Initiated with [AF_INET]172.58.165.141:31792
Thu Nov 21 17:15:01 2024 client9/172.58.165.141:31792 OPTIONS IMPORT: reading client specific options from: ccd/client9
Thu Nov 21 17:15:01 2024 client9/172.58.165.141:31792 MULTI_sva: pool returned IPv4=10.8.0.2, IPv6=(Not enabled)
Thu Nov 21 17:15:01 2024 client9/172.58.165.141:31792 MULTI: Learn: 10.8.0.2 → client9/172.58.165.141:31792
Thu Nov 21 17:15:01 2024 client9/172.58.165.141:31792 MULTI: primary virtual IP for client9/172.58.165.141:31792: 10.8.0.2
Thu Nov 21 17:15:02 2024 client9/172.58.165.141:31792 PUSH: Received control message: ‘PUSH_REQUEST’
Thu Nov 21 17:15:02 2024 client9/172.58.165.141:31792 SENT CONTROL [client9]: ‘PUSH_REPLY,route 10.1.0.0 255.255.0.0,redirect-gateway def1 bypass-dhcp,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-256-GCM’ (status=1)
Thu Nov 21 17:15:02 2024 client9/172.58.165.141:31792 Data Channel: using negotiated cipher ‘AES-256-GCM’
Thu Nov 21 17:15:02 2024 client9/172.58.165.141:31792 Outgoing Data Channel: Cipher ‘AES-256-GCM’ initialized with 256 bit key
Thu Nov 21 17:15:02 2024 client9/172.58.165.141:31792 Incoming Data Channel: Cipher ‘AES-256-GCM’ initialized with 256 bit key
Working
Thu Nov 21 18:15:01 2024 client9/172.58.165.141:31792 TLS: soft reset sec=0 bytes=322152/-1 pkts=1674/0
Thu Nov 21 18:15:02 2024 client9/172.58.165.141:31792 VERIFY OK: depth=1, CN=FreePBX
Thu Nov 21 18:15:02 2024 client9/172.58.165.141:31792 VERIFY OK: depth=0, CN=client9
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_VER=2.4.9
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_PLAT=linux
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_PROTO=2
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_NCP=2
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_LZ4=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_LZ4v2=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_LZO=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_COMP_STUB=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_COMP_STUBv2=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 peer info: IV_TCPNL=1
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 WARNING: ‘link-mtu’ is used inconsistently, local=‘link-mtu 1542’, remote=‘link-mtu 1570’
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 WARNING: ‘cipher’ is used inconsistently, local=‘cipher BF-CBC’, remote=‘cipher AES-128-CBC’
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 WARNING: ‘auth’ is used inconsistently, local=‘auth SHA1’, remote=‘auth SHA256’
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 Outgoing Data Channel: Cipher ‘AES-256-GCM’ initialized with 256 bit key
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 Incoming Data Channel: Cipher ‘AES-256-GCM’ initialized with 256 bit key
Thu Nov 21 18:15:04 2024 client9/172.58.165.141:31792 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA