Almost four years since I learned about APIBAN from @apiban and posted how to use it with FreePBX here. Check that thread for background.
Yesterday, the project announced a new client that integrates APIBAN with fail2ban, just in time for #FridayFun.
Initially I started testing with my home system running the FreePBX 16 Distro. For reasons eplained below, this is less than ideal.
Starting with a FreePBX 17 system installed with the official Debian 12 install script, step one is to disable fail2ban email notifications if it’s enabled. Step 2 is to increase the fail2ban ban time to at least 7 days, the apiban client does a full refresh weekly, so you don’t want rules to expire before the flush happens. I’m using a value of 610,000 seconds, just over 7 days.
I found my old APIBAN key in the file /usr/local/bin/apiban/config.json but if you need to, you can recover an old key using this page.
After a quick review of the install script, I ran the one line command
curl -sSL https://raw.githubusercontent.com/apiban/apiban-fail2ban/main/install.sh | bash -s -- APIBANKEY
This is a low spec VM from vultr, so it took several minutes for the install to complete. While waiting, I could monitor the progress of the initial sync with the command
fail2ban-client status asterisk-iptables
where I would see the banned total steadily increment until it stopped at
Status for the jail: asterisk-iptables
|- Filter
| |- Currently failed: 0
| |- Total failed: 0
| `- File list: /var/log/asterisk/fail2ban
`- Actions
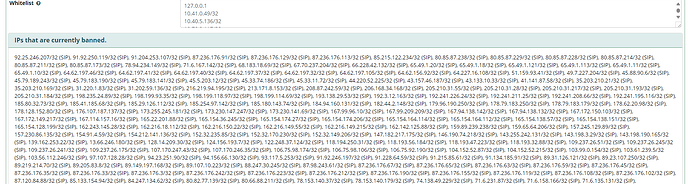
|- Currently banned: 2096
|- Total banned: 2096
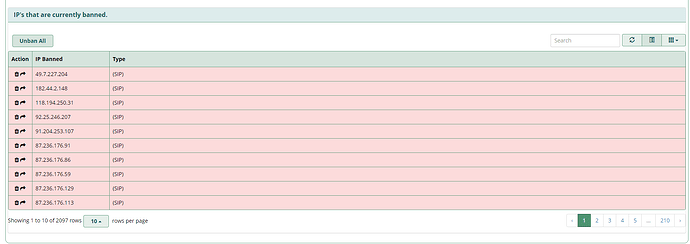
Using this new APIBAN client works a bit more smoothly with the FreeBPX GUI, as now the banned IPs are viewable and controllable directly in the FreePBX Firewall module GUI. Browsing to Connectivity, Firewall, Intrusion Detection tab, we can see all of the current fail2ban bans
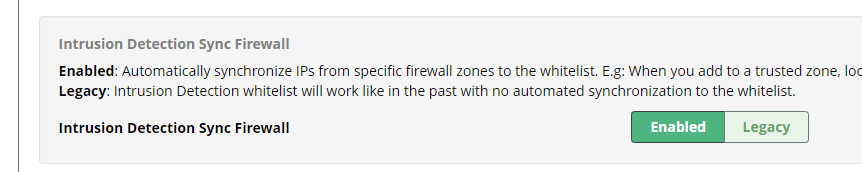
edit - If you don’t see this display, you’ll need to enable Intrusion Detection Sync Firewall under Firewall → Advanced → Advanced Settings
As before I will continue to monitor in the coming days to see how things work.
Huge thanks to Fred Posner/@apiban and the other fine folks there for providing this service!