Hello,
Does anyone know the source of this issue?
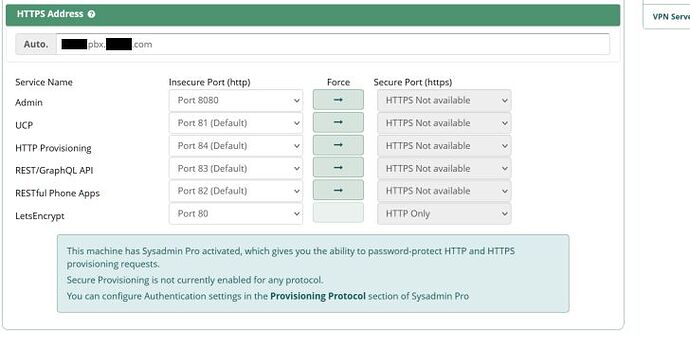
LetsEncrypt Generation Failure
Unable to update challenge :: authorization must be pending
Requested 'http://sitepbx.site.com//.freepbx-known/a2c02700---------------------0625be6' - 403 Forbidden Forbidden You don't have permission to access /.freepbx-known/a2c02700---------------------0625be6 on this server.
The FreePBX Firewall is not enabled.
The LetsEncrypt servers only send challenge queries to port 80. Certificate requests will fail if public access via port 80 is not available.
Processing: sitepbx.site.com, Local IP: 127.0.0.1, Public IP: 99.—.—.217
Self test: trying http://sitepbx.site.com/.freepbx-known/a2c02700---------------------0625be6
Self test: received a2c02700---------------------0625be6
Requested ‘http://sitepbx.site.com//.freepbx-known/a2c02700---------------------0625be6’ -
403 Forbidden
Forbidden
You don’t have permission to access /.freepbx-known/a2c02700---------------------0625be6
on this server.
Getting list of URLs for API
Requesting new nonce for client communication
Account already registered. Continuing.
Sending registration to letsencrypt server
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/new-acct
Account: https://acme-v02.api.letsencrypt.org/acme/acct/3---------0
Starting certificate generation process for domains
Requesting challenge for sitepbx.site.com
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/new-order
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/5------------0
Got challenge token for sitepbx.site.com
Token for sitepbx.site.com saved at /var/www/html/.well-known/acme-challenge/guBMq-----------------------------------------IcO1Llfxo and should be available at http://sitepbx.site.com/.well-known/acme-challenge/guBMq-----------------------------------------IcO1Llfxo
Sending request to challenge
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/5------------0/eAQGQg
Verification pending, sleeping 1s
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/5------------0/eAQGQg
–Firewall disabled to narrow down the cause of the issue.
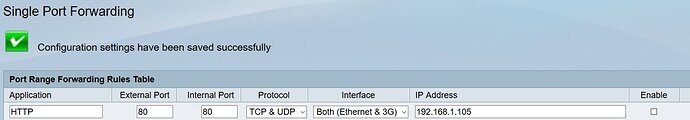
– HTTP port forwarded for both tcp and udp to 192.168.1.105
–VM on bridge mode
– Content of etc/httpd/conf.d/schmoozecom.conf for port 80:
Listen 80
<VirtualHost *:80>
Alias /.well-known /var/www/html/.well-known
Alias /.freepbx-known /var/www/html/.freepbx-known
RewriteEngine on
RewriteRule ^/.(well-known|freepbx-known)/ - [H=text/plain,L]
RewriteRule (^.|/.) - [F]
DocumentRoot /invalid/folder/name
Thanks