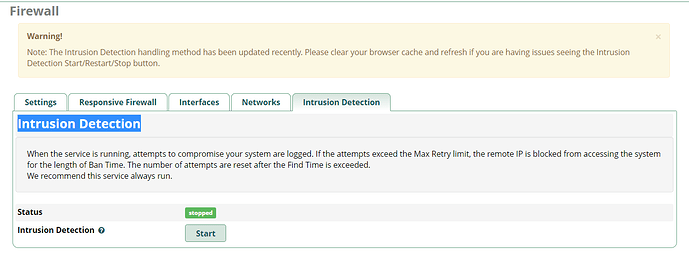
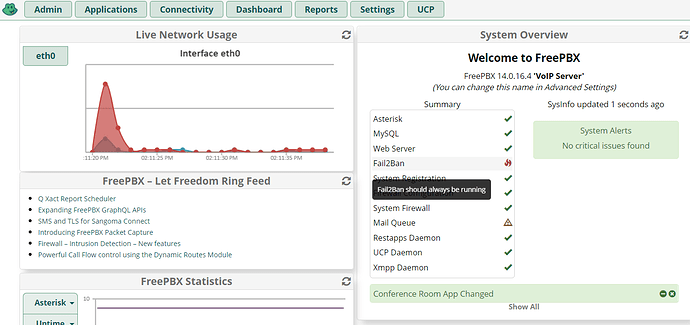
Hey Guys I have the firewall enabled, however the Intrusion detection will not
start. I click on start and it immediately goes to stopped. also on the main page the fai2band showsTry running
fwconsole chown
fwconsole reload
service fail2ban restart
And post the output of the last command
[root@freepbx ~]# fwconsole chown
Taking too long? Customize the chown command, See http://wiki.freepbx.org/display/FOP/FreePBX+Chown+Conf
Setting Permissions…
Setting base permissions…^[[A^[[A^[[B^[[BDone
Setting specific permissions…
43687 [============================]
Finished setting permissions
[root@freepbx ~]# fwconsole reload
Reloading FreePBX
Successfully reloaded
[root@freepbx ~]# service fail2band restart
Redirecting to /bin/systemctl restart fail2band.service
Failed to restart fail2band.service: Unit not found.
It is fail2ban not fail2band , post the output of
fail2ban-client -t
systemctl status fail2ban
systemctl status fail2ban
● fail2ban.service - Fail2Ban Service
Loaded: loaded (/usr/lib/systemd/system/fail2ban.service; disabled; vendor preset: disabled)
Active: failed (Result: start-limit) since Sun 2021-02-07 11:47:13 MST; 1min 13s ago
Process: 4589 ExecStart=/usr/bin/fail2ban-client -x start (code=exited, status=255)
Process: 4587 ExecStartPre=/bin/mkdir -p /var/run/fail2ban (code=exited, status=0/SUCCESS)
Feb 07 11:47:12 freepbx.sangoma.local systemd[1]: fail2ban.service: control process exited, code=exited status=255
Feb 07 11:47:12 freepbx.sangoma.local systemd[1]: Failed to start Fail2Ban Service.
Feb 07 11:47:12 freepbx.sangoma.local systemd[1]: Unit fail2ban.service entered failed state.
Feb 07 11:47:12 freepbx.sangoma.local systemd[1]: fail2ban.service failed.
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: fail2ban.service holdoff time over, scheduling restart.
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: Stopped Fail2Ban Service.
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: start request repeated too quickly for fail2ban.service
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: Failed to start Fail2Ban Service.
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: Unit fail2ban.service entered failed state.
Feb 07 11:47:13 freepbx.sangoma.local systemd[1]: fail2ban.service failed.
[root@freepbx ~]#
[root@freepbx ~]# fail2ban-client -t
Usage: /usr/bin/fail2ban-client [OPTIONS]
Fail2Ban v0.8.14 reads log file that contains password failure report
and bans the corresponding IP addresses using firewall rules.
Options:
-c configuration directory
-s socket path
-p pidfile path
-d dump configuration. For debugging
-i interactive mode
-v increase verbosity
-q decrease verbosity
-x force execution of the server (remove socket file)
-h, --help display this help message
-V, --version print the version
Command:
BASIC
start starts the server and the jails
reload reloads the configuration
reload reloads the jail
stop stops all jails and terminate the
server
status gets the current status of the
server
ping tests if the server is alive
help return this output
LOGGING
set loglevel <LEVEL> sets logging level to <LEVEL>. 0
is minimal, 4 is debug
get loglevel gets the logging level
set logtarget <TARGET> sets logging target to <TARGET>.
Can be STDOUT, STDERR, SYSLOG or a
file
get logtarget gets logging target
flushlogs flushes the logtarget if a file
and reopens it. For log rotation.
JAIL CONTROL
add <JAIL> <BACKEND> creates <JAIL> using <BACKEND>
start <JAIL> starts the jail <JAIL>
stop <JAIL> stops the jail <JAIL>. The jail is
removed
status <JAIL> gets the current status of <JAIL>
JAIL CONFIGURATION
set <JAIL> idle on|off sets the idle state of <JAIL>
set <JAIL> addignoreip <IP> adds <IP> to the ignore list of
<JAIL>
set <JAIL> delignoreip <IP> removes <IP> from the ignore list
of <JAIL>
set <JAIL> addlogpath <FILE> adds <FILE> to the monitoring list
of <JAIL>
set <JAIL> dellogpath <FILE> removes <FILE> from the monitoring
list of <JAIL>
set <JAIL> addfailregex <REGEX> adds the regular expression
<REGEX> which must match failures
for <JAIL>
set <JAIL> delfailregex <INDEX> removes the regular expression at
<INDEX> for failregex
set <JAIL> ignorecommand <VALUE> sets ignorecommand of <JAIL>
set <JAIL> addignoreregex <REGEX> adds the regular expression
<REGEX> which should match pattern
to exclude for <JAIL>
set <JAIL> delignoreregex <INDEX> removes the regular expression at
<INDEX> for ignoreregex
set <JAIL> findtime <TIME> sets the number of seconds <TIME>
for which the filter will look
back for <JAIL>
set <JAIL> bantime <TIME> sets the number of seconds <TIME>
a host will be banned for <JAIL>
set <JAIL> usedns <VALUE> sets the usedns mode for <JAIL>
set <JAIL> banip <IP> manually Ban <IP> for <JAIL>
set <JAIL> unbanip <IP> manually Unban <IP> in <JAIL>
set <JAIL> maxretry <RETRY> sets the number of failures
<RETRY> before banning the host
for <JAIL>
set <JAIL> addaction <ACT> adds a new action named <NAME> for
<JAIL>
set <JAIL> delaction <ACT> removes the action <NAME> from
<JAIL>
set <JAIL> setcinfo <ACT> <KEY> <VALUE> sets <VALUE> for <KEY> of the
action <NAME> for <JAIL>
set <JAIL> delcinfo <ACT> <KEY> removes <KEY> for the action
<NAME> for <JAIL>
set <JAIL> actionstart <ACT> <CMD> sets the start command <CMD> of
the action <ACT> for <JAIL>
set <JAIL> actionstop <ACT> <CMD> sets the stop command <CMD> of the
action <ACT> for <JAIL>
set <JAIL> actioncheck <ACT> <CMD> sets the check command <CMD> of
the action <ACT> for <JAIL>
set <JAIL> actionban <ACT> <CMD> sets the ban command <CMD> of the
action <ACT> for <JAIL>
set <JAIL> actionunban <ACT> <CMD> sets the unban command <CMD> of
the action <ACT> for <JAIL>
JAIL INFORMATION
get <JAIL> logpath gets the list of the monitored
files for <JAIL>
get <JAIL> ignoreip gets the list of ignored IP
addresses for <JAIL>
get <JAIL> ignorecommand gets ignorecommand of <JAIL>
get <JAIL> failregex gets the list of regular
expressions which matches the
failures for <JAIL>
get <JAIL> ignoreregex gets the list of regular
expressions which matches patterns
to ignore for <JAIL>
get <JAIL> findtime gets the time for which the filter
will look back for failures for
<JAIL>
get <JAIL> bantime gets the time a host is banned for
<JAIL>
get <JAIL> usedns gets the usedns setting for <JAIL>
get <JAIL> maxretry gets the number of failures
allowed for <JAIL>
get <JAIL> addaction gets the last action which has
been added for <JAIL>
get <JAIL> actionstart <ACT> gets the start command for the
action <ACT> for <JAIL>
get <JAIL> actionstop <ACT> gets the stop command for the
action <ACT> for <JAIL>
get <JAIL> actioncheck <ACT> gets the check command for the
action <ACT> for <JAIL>
get <JAIL> actionban <ACT> gets the ban command for the
action <ACT> for <JAIL>
get <JAIL> actionunban <ACT> gets the unban command for the
action <ACT> for <JAIL>
get <JAIL> cinfo <ACT> <KEY> gets the value for <KEY> for the
action <ACT> for <JAIL>
Report bugs to https://github.com/fail2ban/fail2ban/issues
The ‘distro’ distributes a very old version of fail2ban without the option -t (for test), try
fail2ban-client status
fail2ban-client start
fail2ban-client status
Edit:
It would seem that you are using the distro, so I can’t help you further as fail2ban seems to be entangled within the sysadmin/firewall modules neither of which I use.
[root@freepbx ~]# fail2ban-client status
ERROR Unable to contact server. Is it running?
[root@freepbx ~]# fail2ban-client start
ERROR No file(s) found for glob /var/log/asterisk/zulu_out.log
ERROR Failed during configuration: Have not found any log file for zulu jail
[root@freepbx ~]# fail2ban-client status
ERROR Unable to contact server. Is it running?
A clue. Try running
touch /var/log/asterisk/zulu_out.log
chown asterisk:asterisk /var/log/asterisk/zulu_out.log
And then restart fail2ban
Thanks this worked
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.