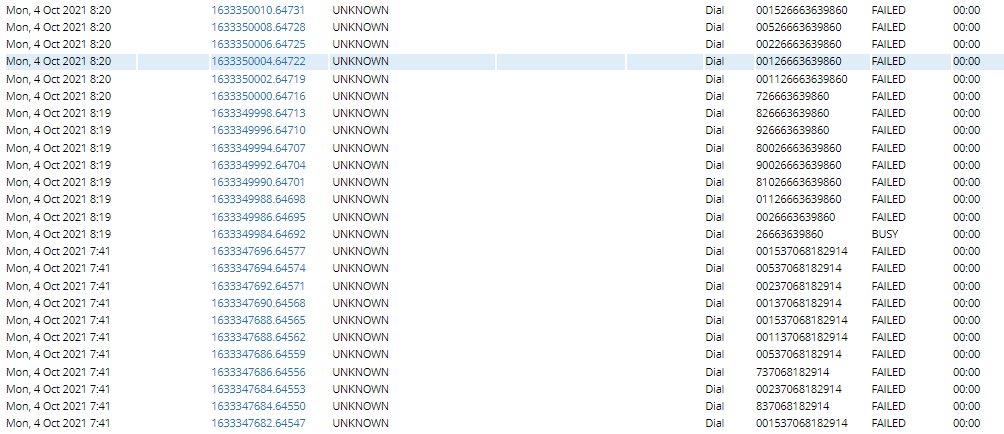
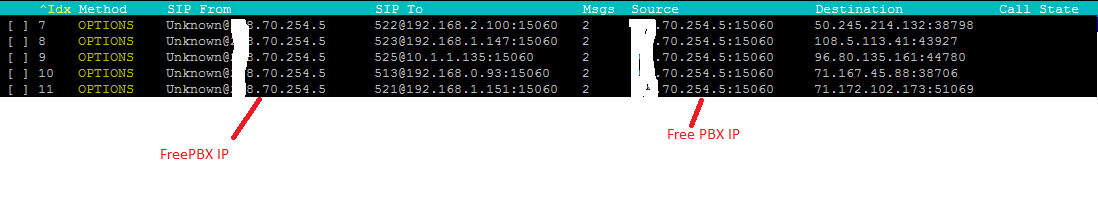
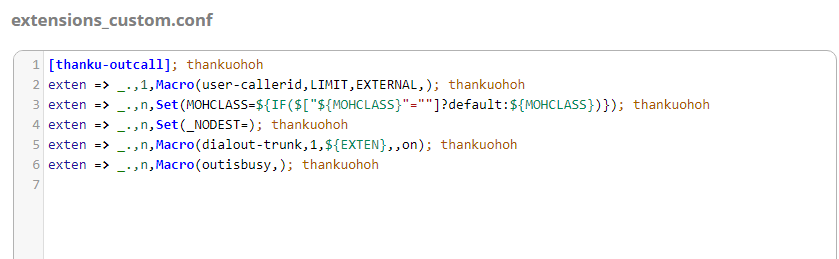
Hi All, I’m using freepbx version 15.0.6 version. It seems my freepbx has been hacked. I see a new dial plan entry has been added in extensions_custom.conf file. I removed it but after a day again it’s there. I changed Web and SSH password and secured web and ssh to not access from outside but still someone is able to manipulate extensions_custom.conf file I’ve attached freepbx and SNGREP logs. Below are asterisk logs. Please advise.
Asterisk Log - FreePBX Pastebin
Did you remove it? Did you change all your access passwords to the GUI and SSH?
How are people still getting hit with this hack?
Yes I changed all passwords and and I made http and SSH secure via iptables not to access other than authorized IP’s. But still this dial plan entry written on the file.
You should, uhm, REMOVE IT NOW!
Can you please tell me what is UHM?
It is unimportant. You need to remove that stuff from extensions_custom.conf
I already removed that stuff from extensions_custome.conf. If I removed after a day again it’s there.
Then they have compromised your box if you have changed your passwords for the admin GUI and SSH.
Then you need to install again from scratch. The system cannot be deemed safe again
@BlazeStudios I already changed SSH and GUI passwords. And I secured them through iptables to not to access from unauthorized IP. Still how can someone get into the system?
Because they dropped scripts and other things on the server that gives them access at the server level. So it doesn’t matter you made these changes, the system is making the changes/calls from the inside.
It’s hard to rebuild a system again from scratch if there is a lot of data on it. Anything I can check that?
Here is a detailed walkthrough about this known exploit --> https://rucore.net/en/how-to-crack-your-asterisk/. It’s been around for awhile now. I’m thankful I don’t directly expose my server to the Internet, since it can be a can of worms.
In case anyone’s concerned about this, the bug was fixed in November 2019. https://issues.freepbx.org/browse/FREEPBX-20791
That means if you have updated your FreePBX server within the last 22 months you will not be vulnerable to this bug.
Launch : fwconsole validate
If you’ve got some doubts, just remove this devil context.
Don’t forget to update all modules and O.S with
fwconsole ma updateall
yum update -y
Launch a backup before.
I’ve seen this before - there seems to be a somewhat easy fix. First make sure your firewall is correctly setup and fail2ban is working. Second, go into SIP settings and turn allow sip guests to NO.
For some reason that setting is on by default and yes there are uses for it, just not for most regular systems.
Is there some reason that your machine has to be connected directly to the internet and is not behind a NAT router?
There are always going to be exploits in Linux, Asterisk, and FreePBX. Some are known and get patched, and some are unknown (and don’t).
At this point, I’d suggest that you (1) wipe the machine, (2) reinstall, (3) set-up your machine behind a NAT router (and DO NOT FORWARD ANY PORTS), (4) set-up Iptables manually to keep out all traffic other than what is essential to run it.
The recommendation to set “Allow SIP Guests” to “No” is a common one, but it is nearly always wrong. Not allowing SIP Guests basically just means that you won’t see attacks in the logfiles. The safer approach is to allow SIP Guests, allow anonymous inbound SIP Calls, and then create a “catchall” inbound route, leave the DID and CID blank, and route calls to “Terminate Calls: Hangup”.
I don’t take any credit for the above, but one of the members of the community with far more experience than me once posted a lengthy explanation as to why the above is far more secure.
All of this advice used to be in the Wiki, but the former community manager (who left Sangoma for ClearlyIP) felt it was not useful and deleted it.
(NAT is not a firewall!)
I think you’re mistaken.
A NAT Router includes a firewall that only opens ports in response to outbound traffic. I think that it’s more accurate to say that NAT Router is not a very good firewall.
And again, see step #4: “set-up Iptables manually to keep out all traffic other than what is essential to run it.”
For more on NAT being a form of firewall, see these links:
https://nordvpn.com/blog/what-is-nat-firewall/#:~:text=A%20Network%20Address%20Translation%20(NAT,IP%20addresses%20to%20the%20internet.
https://en.wikipedia.org/wiki/Network_address_translation
https://www.abuseat.org/nat.htmlAnd there I was thinking that phone calls were essentially lots of “inbound traffic” and that many SIP penetrations came also from the outside, and over these same ports.