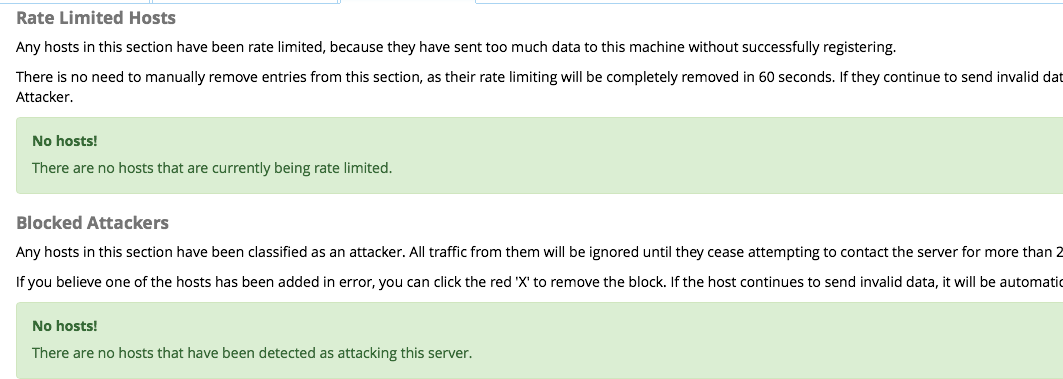
[2018-06-12 19:12:33] WARNING[8116]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[17553]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[4843]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[28905]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[12778]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[12778]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[14920]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[20950]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[1662]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[20810]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[24033]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[5178]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[30275]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[14604]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[30275]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[4721]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[18980]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[11250]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[7316]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[7316]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[8116]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[17553]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[4843]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[28905]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[12778]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[14530]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[14920]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[20950]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[1662]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[20810]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[24033]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[5178]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
[2018-06-12 19:12:33] WARNING[14604]: res_pjsip_registrar.c:963 registrar_on_rx_request: Endpoint ‘anonymous’ has no configured AORs
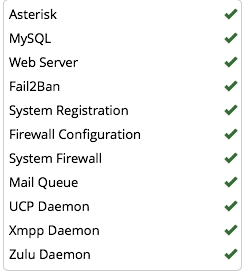
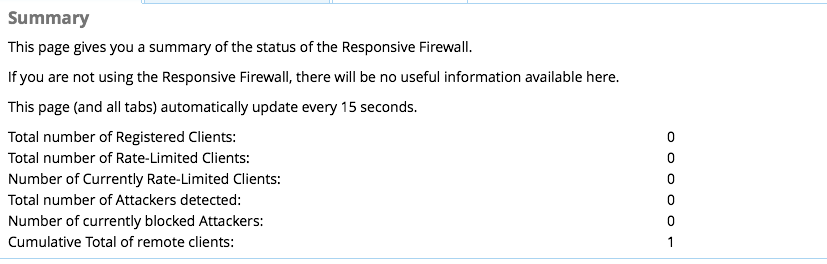
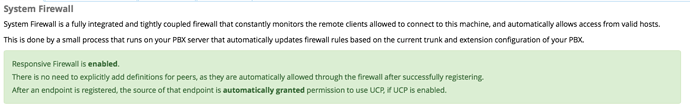
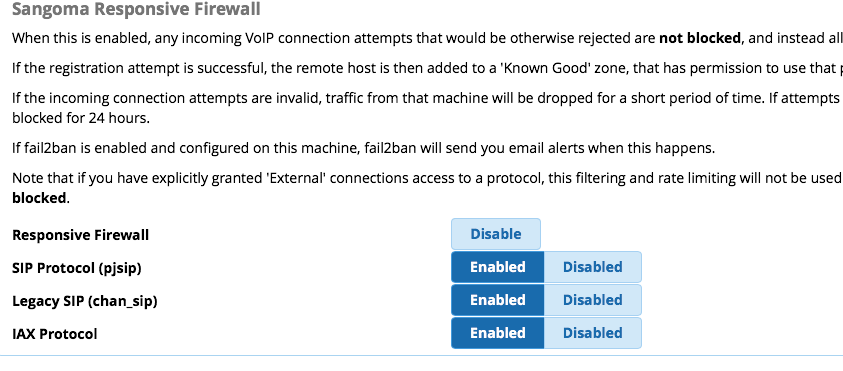
This just floods the asterisk CLI what can I do to stop it?