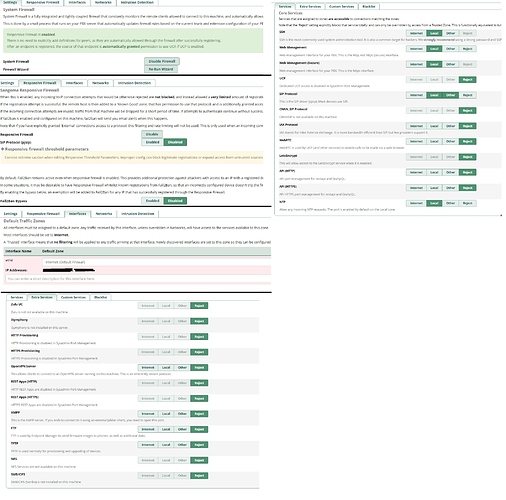
hi, i am planning to make my freepbx more secure and allow access only from specific ip, so on the screenshot there is my configuration and i have added my voip provider as Other Network and my office ip as Trusted Network so i have allowed web gui admin only from Trusted Network not from Other Network. Is this the best config?. Thanks
That looks correct. If you’re still fuzzy on details, check out this vid Open Source Pro Tips #2 - Firewall Basics
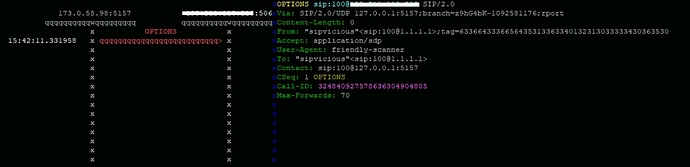
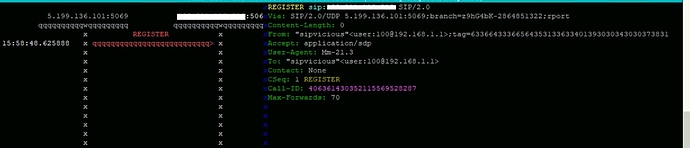
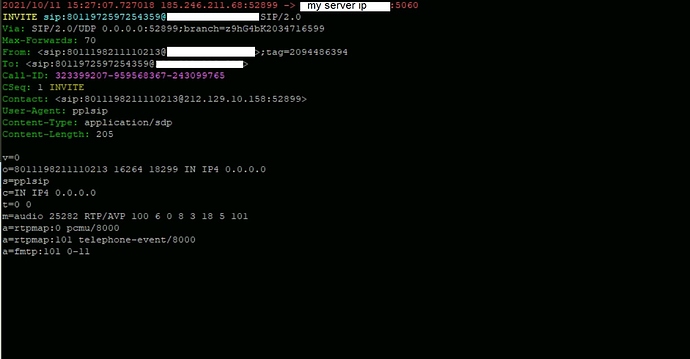
i have blocked everything except my ip but why am i seeing this: ![]()
why they are still attacking, i blocked everything?![]()
IIRC, sngrep captures traffic before iptables. Do you see these INVITEs or REGISTERs in asterisk?
pjsip set logger on
Or if you are using ChanSIP
sip set debug on
Look at the Msgs col in sngrep, it will tell you how many packets are in the SIP dialog. When the local firewall is working as expected, you will see the inbound packet in sngrep, but no reply back from Asterisk.
i am not using sip server port 5060, i am using different one, does it mean that they are trying to attack port 5060 as you see in the picture?
As you can see, Asterisk did not respond to these requests, which indicates that the firewall is working as expected.
These are SIP scanners which are scanning the entire internet, and whatever system that responds, the “friendly scanner” will start a brute force attack.
The reason you are seeing this traffic in sngrep even tho Asterisk is not running PJSIP or ChanSIP on 5060, is because sngrep captures any (unencrypted) SIP traffic sent/received through the network interface. Try it yourself; Grab any SIP client and try to register against your.server.ip:1234 and watch sngrep…
where can i see that the asterisk did not respond? I am just thinking if its worth it to disable responsive firewall and allow only from specific ip or enable firewall responsive. Which one do you prefer and if i enable responsive firewall is there any chance my freepbx will be hacked ? Thanks again for your time
The simple existance of 1 in the msgs column implicitly states that there was no response.
The only way you will stop seeing those UDP/5060 connection attempts is by adding a firewall before your PBX that will filter them out, Machines that haven’t been responding for years still get slow but steady attempts to UDP/5060.
Any chance for the attacker to hack sip server if i leave it open to the world with responsive firewall enabled?
Technically, if there is no process running that would handle such a udp/5060 connection . , it is hard to imagine any problems with or without the responsive firewall running. BUT often other ports than 5060 are attacked, choose your port carefully and ideally protect your PBX with an external firewall that only accepts that port for your SIP connectiuons, use TCP or TLS for even better protection.
Is it more secure sip udp or webrtc with https and 8089 port open, because i am thinking if its better to use webrtc or softphones, thanks
Any connection using a 'secure ’ connection is pretty well secure so webrtc is good as is TLS.
Connections now need to come to a certified domain and not just an IP, there is reason to use obscure domains other than your main domain for such connections but that is a completely different kettle of ghoti.
This topic was automatically closed 31 days after the last reply. New replies are no longer allowed.