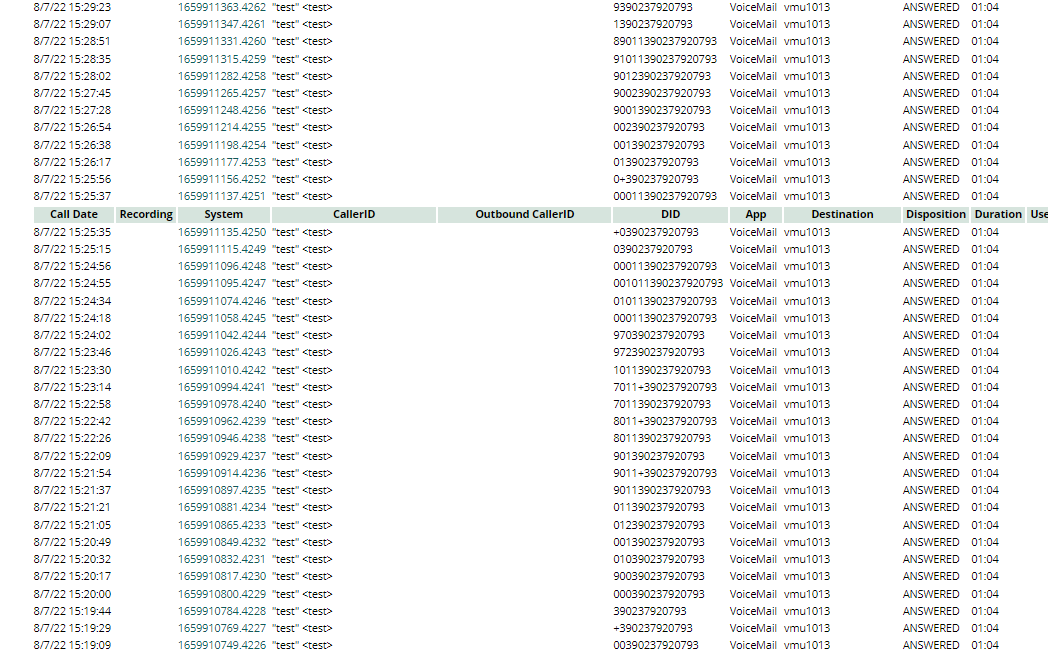
I noticed a string of attempted fraudulent calls in the CDRs:
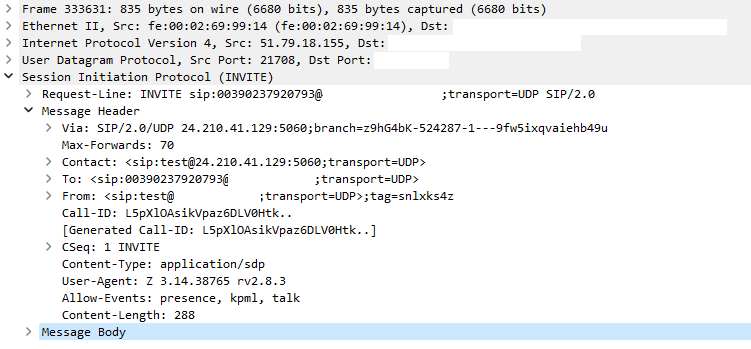
Here is a sample incoming INVITE:
pjsip responded correctly to the INVITE with a 401 (to which the attacker did not further reply) but accepted the call anyhow, apparently because the user field of the From header (or perhaps the Contact header) matched the trunk name! This was an ordinary trunk (Authentication Outbound and Registration Send) that I had set up for testing.
I don’t know whether this is a bug or an intentional feature (Asterisk version is 16.19.0). If the latter, you should take care to use obscure trunk names that would be very unlikely for an attacker to guess. This is especially important for trunks with a Context that permits outgoing calls.
I believe it’s unrelated, but note that the address in the Via header differs from the source address. If your trunk has Force rport set to No (default is Yes), this would allow an attacker who could spoof IP source addresses to also bypass your firewall (hardware or FreePBX) by sending an address that you have whitelisted. If it also has Context from-internal, they could make arbitrary calls without authentication.