malcolmd
November 19, 2018, 6:27pm
41
Howdy,
w.r.t. use of self-signed certificates on a Yealink T-5x…I’ve a T-58V with firmware 58.80.0.10.
If you use certificates that are out of date (before or after/expired), things are a no go.
After running the ast_tls_cert script, you’ll have a ca.crt file and a number of other files.
The ca.crt file should be loaded into the Yealink’s list of Trusted Certificates.
That should handle things for the Yealink in its default state, and Asterisk, with the default PJSIP settings w.r.t. TLS.
…also, I know I’m late to the party here.
hardocp
November 19, 2018, 6:57pm
42
Since i am going to try and use the LE cert to avoid the whole self sign issue – if i go into etc/asterisk/keys i see the “certificatename”.crt
Assume that is the file i upload into the phone
Any other settings need to be adjusted on the Trusted Cert page?
My phone is a T54s Firmware Version 70.84.0.10
malcolmd
November 19, 2018, 7:04pm
43
I didn’t have to make any modifications on the Trusted Cert page aside of loading the ca.crt file, where I was putting a self-signed certificate into Asterisk.
I can’t tell you exactly what’s going to happen here, because I don’t have a publicly signed cert running against my test server to which I’m connecting the Yealink, and I’m not running your Yealink firmwre version or exact model. I can only speak to my general experience.
One prerequisite, as it pertains to telephones, is time. Deskphones don’t have batteries in them, for good reasons. So, they have to be set to an accurate clock, not January 1, 1970, in order to validate anything using OpenSSL. Make sure your device was able to source time from an NTP server, or via some other method.
Where a server has a publicly signed certificate on it, that includes the full chain, and where a client contains a root CA that can be used to validate that server certificate, everything should be copacetic. The full chain is important, because most client devices that aren’t web browsers, i.e. telephones, will call openssl to validate the server’s cert. OpenSSL will be pointed at some built-in bundle of root CAs, stored on the phone, that it’ll search against. If it finds one that’ll work, everything’s golden.
If the server doesn’t have a publicly signed certificate, your options are to either tell the phone to ignore server certificate validation, or to load the server’s root CA onto the phone - that’s what I did by dropping the ca.crt file from ast_tls_cert into the phone’s web page, Trusted Certificates.
sorvani
November 19, 2018, 8:26pm
44
Any firmware after X.80.X.X is supposed to have the LE root cert.
hardocp
November 19, 2018, 8:38pm
45
Well i just dont know then
Can you guys recommend someone who i can pay for an hour or two of their time to vpn into my FPBX system and help me finish this up?
sorvani
November 19, 2018, 8:42pm
46
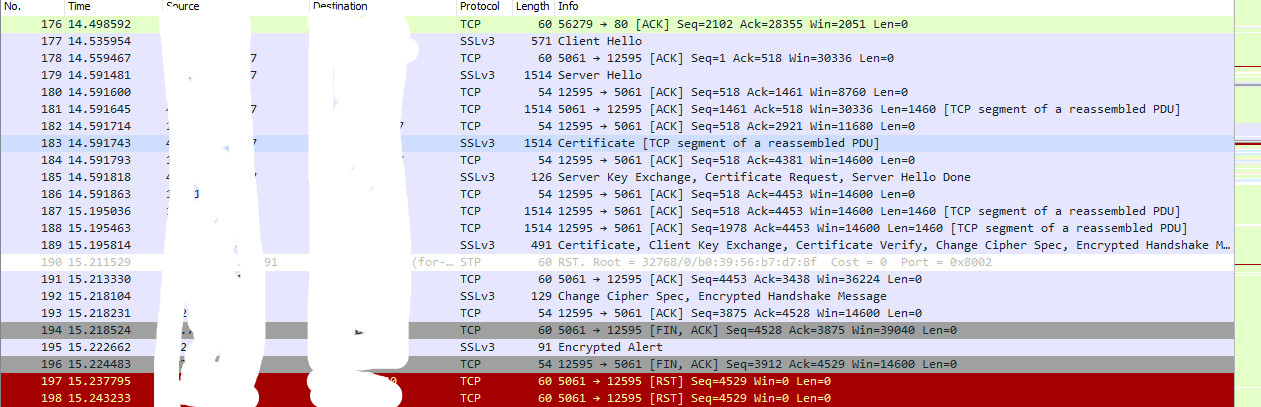
That said, my above issue proves that it does not work. The T46G on the desk in front of me right now has firmware 28.83.0.50.
But if I put a remote address book on a button using https it will fail to load.
<134>Nov 19 13:51:57 GUI [1262:1294]: DIR <6+info > 117.929.497:CContactRemoteAction::Exec()
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.930.414:[DCMN]create handle success.
<134>Nov 19 13:51:57 GUI [1262:1294]: TASK<6+info > 117.933.215:set download option ssl trust[1],maxdownload size[1572864] connect timeout[10],download timeout[0]
<134>Nov 19 13:51:57 GUI [1262:1294]: TASK<6+info > 117.934.181:http download url[https://pbx.mydomain.com/ylmenu.xml] user[****] passwd[****] http_autp[0] method[0]
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.934.515:[DCMN]download to file...
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.934.676:[DCMN]Use new short connect.
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.935.491:[DCMN]HTTP request use auth = 0.
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.935.901:[DCMN]ssl cipher:AES:!ADH:!LOW:!EXPORT:!NULL
<134>Nov 19 13:51:57 GUI [1262:1294]: WIND<6+info > 117.936.248:[DCMN]I will write to file: /tmp/RemoteDirectory.0000000165.xml
<134>Nov 19 13:51:57 GUI [1262:1262]: POPB<6+info > 117.947.799:CMsgBoxManager::AddMessageBox
<134>Nov 19 13:51:57 GUI [1262:1262]: POPB<6+info > 117.948.336:Add CCommonMessageBox::PrintMsgBoxInfo: ?`23Loading, please wait...
<134>Nov 19 13:51:57 GUI [1262:1262]: POPB<6+info > 117.948.754:CMsgBoxManager Update MsgBox Info
<134>Nov 19 13:51:57 GUI [1262:1262]: BKLT<6+info > 117.949.455:BackLightManager::AddEvent [1]
<134>Nov 19 13:51:57 GUI [1262:1262]: UIMG<6+info > 117.967.509:[UIManager] Dialog(CDlgPickupMenu) is not cached or not used!
<134>Nov 19 13:51:57 GUI [1262:1262]: IDUI<6+info > 117.968.260:QEvent::Hide
<134>Nov 19 13:51:57 GUI [1262:1262]: DIRU<6+info > 117.970.784:OnBrowserUIShow(FrameList:0x24bdd0)
<134>Nov 19 13:51:57 GUI [1262:1262]: DIRU<6+info > 117.971.640:CDirectoryListDelegate::OnLoadData(0x24bdd0 0 5)
<134>Nov 19 13:51:57 GUI [1262:1262]: DIRU<6+info > 117.974.414:CCommonDirCtrl::LoadListData(Index:0 Count:5)
<134>Nov 19 13:51:57 GUI [1262:1262]: DIRU<6+info > 117.974.889:Dir_GetContactListByGroupId(Type:5 GroupId:2 Count:5 Index:0)
<134>Nov 19 13:51:57 GUI [1262:1262]: DIR <6+info > 117.975.430:GetContactList pData->m_nTotalCount[0]
<134>Nov 19 13:51:57 GUI [1262:1262]: DIRU<6+info > 117.975.826:CCommonUIHelper::FillData(TotalCount:0 GetCount:0 Index:0)
<134>Nov 19 13:51:58 GUI [1262:1294]: WIND<6+info > 118.008.537:[DCMN]CURL Info: TLSv1.2 (OUT), TLS handshake, Client hello (1):
<134>Nov 19 13:51:58 ipp [1145]: IIPP<6+info > 118.013.264:EptEvent event 2 streamid 4 slot_num 65535 index 0
<134>Nov 19 13:51:58 GUI [1262:1294]: WIND<6+info > 118.074.764:[DCMN]CURL Info: TLSv1.2 (IN), TLS handshake, Server hello (2):
<134>Nov 19 13:51:58 GUI [1262:1294]: WIND<6+info > 118.075.933:[DCMN]CURL Info: TLSv1.2 (IN), TLS handshake, Certificate (11):
<134>Nov 19 13:51:58 GUI [1262:1294]: WIND<6+info > 118.175.279:[DCMN]CURL Info: TLSv1.2 (IN), TLS handshake, Server key exchange (12):
<134>Nov 19 13:51:58 GUI [1262:1262]: BKLT<6+info > 118.208.114:Operation[1] status[0] IsFailBackMode[0] to power saving
<134>Nov 19 13:51:58 GUI [1262:1262]: GBIH<6+info > 118.209.767:Global Key Up:(1000031)
<134>Nov 19 13:51:58 GUI [1262:1262]: BKLT<6+info > 118.210.509:BackLightManager::AddEvent [1]
<134>Nov 19 13:51:58 GUI [1262:1262]: BKLT<6+info > 118.225.374:Operation[0] status[0] IsFailBackMode[0] to power saving
<134>Nov 19 13:51:58 GUI [1262:1262]: BKLT<6+info > 118.226.493:Operation[1] status[0] IsFailBackMode[0] to power saving
<134>Nov 19 13:51:58 GUI [1262:1294]: WIND<6+info > 118.270.908:[DCMN]CURL Info: TLSv1.2 (IN), TLS handshake, Server finished (14):
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.920.802:[DCMN]CURL Info: TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.923.071:[DCMN]CURL Info: TLSv1.2 (OUT), TLS change cipher, Client hello (1):
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.927.044:[DCMN]CURL Info: TLSv1.2 (OUT), TLS handshake, Finished (20):
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.928.590:[DCMN]CURL Info: Unknown SSL protocol error in connection to pbx.mydomain.com:443
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.934.848:[DCMN]Connect is short Cleanup curl.
<131>Nov 19 13:52:30 GUI [1262:1294]: WIND<3+error > 150.936.293:[DCMN]download common error, errcode:35.
<134>Nov 19 13:52:30 GUI [1262:1294]: WIND<6+info > 150.936.834:[DCMN]download common error, remove file.
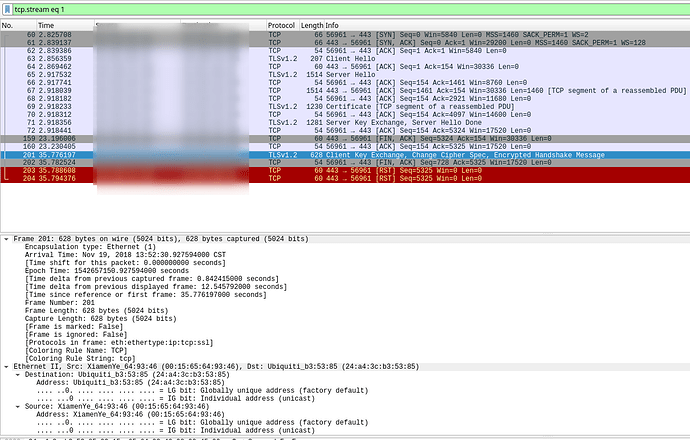
The PCAP captured by the phone itself shows the Server key exchange and hello completing, which matches the above log.
Then some weird 20+ seconds delay while it fails to figure out the client key and cipher.
sorvani
November 19, 2018, 8:43pm
47
I’m testing a T42S right now. it seems to be working. Give me a minute.
sorvani
November 19, 2018, 9:53pm
48
Ok, just tested everything and figured it out.
The Yealink T4XS series only work when you set the SSL method to SSLv2 or SSLv3
Once I changed that and rebooted the phone registered.
I then changed the RTP encryption settings in the extension I was testing.
And updated the phone to this.
account.1.sip_server.1.address = pbx.mydomain.com
account.1.sip_server.1.port = 5061
account.1.password = yourpassword
account.1.user_name = yourextension
account.1.sip_server.1.transport_type = 2
account.1.srtp_encryption = 2
hardocp
November 19, 2018, 11:44pm
49
Oh how i was soo excited to get this working finally – alas was not meant to be
sorvani
November 20, 2018, 12:35am
50
What firmware are you on? The commercial EPM firmware is quite a ways back last time I looked.
hardocp
November 20, 2018, 12:49am
51
Firmware Version 70.84.0.10
sorvani
November 20, 2018, 2:09am
52
I do not have any T5 series to test or ir would work on it.
tm1000
November 20, 2018, 3:30am
53
There is also a ticket to support tls 1.1 and 1.2 in sip settings. Coming soon.
sorvani
November 20, 2018, 5:54am
54
I’m not worried about FreePBX supporting it. I’m more worried about the phone vendors.
hardocp
November 20, 2018, 3:33pm
55
I believe that i have confirmed that this is a Yealink issue
I have now installed 2 seperate certs installed – Comodo and LE – wanted to ensure it was not a cert issue
I have also downloaded the t-max dialer softphone for testing (needed a softphone which allowed TLS / SRTP)
i am able to connect to my endpoint using the softphone and run an echo test etc… seems to be fine
the ssl method is set to default – which appears to be TLSv1
i have a ticket in with yealink – will report back when i hear from them
system
November 27, 2018, 3:33pm
56
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.