You need to show a debug with the commands I gave earlier and post the output
Ok – i tried that again – and again nothing shows in the cli
I think the reason is as Andrew said above that I won’t see requests on asterisk if TLS negotiation can’t happen
I just dont understand why the darn certificates wont negotiate a connection
I must be missing something simple here in my setup – it cannot be this hard to set this up
OK so do this from the system CLI (not Asterisk)
tcpdump -nttv -s 0 -i eth0 port 5066
Replace eth0 with your network interface if it is not eth0 and the port to whatever you have TLS on now. Show that output.
Also. You don’t ever need to add certificates to a phone if they are valid (not self signed) certificates. Phones are like web browsers. Do you have to install a certificate on your computer or phone for every site you visit? No. Asterisk uses the root bundle on your server the same as the phone uses the root bundle in it unless you uploaded your own and screwed it up.
You then never connect to the server using an IP address you have to use the FQDN
You should factory reset your phone
1542582411.437694 IP (tos 0x0, ttl 49, id 23412, offset 0, flags [DF], proto TCP (6), length 52)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [S], cksum 0xfa38 (correct), seq 1009689710, win 5840, options [mss 1460,nop,nop,sackOK,nop,wscale 2], length 0
1542582411.437765 IP (tos 0x60, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [S.], cksum 0xa1fe (incorrect -> 0x4996), seq 1873667486, ack 1009689711, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
1542582411.454591 IP (tos 0x0, ttl 49, id 23413, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0xf6c4 (correct), ack 1, win 1460, length 0
1542582411.947293 IP (tos 0x0, ttl 49, id 23414, offset 0, flags [DF], proto TCP (6), length 557)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [P.], cksum 0x69f6 (correct), seq 1:518, ack 1, win 1460, length 517
1542582411.947382 IP (tos 0x60, ttl 64, id 47367, offset 0, flags [DF], proto TCP (6), length 40)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [.], cksum 0xa1f2 (incorrect -> 0xf986), ack 518, win 237, length 0
1542582411.953140 IP (tos 0x60, ttl 64, id 47368, offset 0, flags [DF], proto TCP (6), length 2960)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [.], cksum 0xad5a (incorrect -> 0xf6d9), seq 1:2921, ack 518, win 237, length 2920
1542582411.953178 IP (tos 0x60, ttl 64, id 47370, offset 0, flags [DF], proto TCP (6), length 2960)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [P.], cksum 0xad5a (incorrect -> 0x3308), seq 2921:5841, ack 518, win 237, length 2920
1542582411.965850 IP (tos 0x0, ttl 49, id 23417, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0xdb15 (correct), ack 4381, win 3650, length 0
1542582411.965932 IP (tos 0x60, ttl 64, id 47372, offset 0, flags [DF], proto TCP (6), length 391)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [P.], cksum 0xa351 (incorrect -> 0xb073), seq 5841:6192, ack 518, win 237, length 351
1542582411.965952 IP (tos 0x0, ttl 49, id 23418, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0xd287 (correct), ack 5841, win 4380, length 0
1542582411.978096 IP (tos 0x0, ttl 49, id 23419, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0xce4e (correct), ack 6192, win 5110, length 0
1542582412.626700 IP (tos 0x0, ttl 49, id 23420, offset 0, flags [DF], proto TCP (6), length 1500)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0x198e (correct), seq 518:1978, ack 6192, win 5110, length 1460
1542582412.627217 IP (tos 0x0, ttl 49, id 23421, offset 0, flags [DF], proto TCP (6), length 1921)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [P.], cksum 0xa94b (incorrect -> 0xdac2), seq 1978:3859, ack 6192, win 5110, length 1881
1542582412.627251 IP (tos 0x60, ttl 64, id 47373, offset 0, flags [DF], proto TCP (6), length 40)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [.], cksum 0xa1f2 (incorrect -> 0xd416), ack 3859, win 289, length 0
1542582412.629959 IP (tos 0x60, ttl 64, id 47374, offset 0, flags [DF], proto TCP (6), length 1426)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [P.], cksum 0xa75c (incorrect -> 0xaf4c), seq 6192:7578, ack 3859, win 289, length 1386
1542582412.630212 IP (tos 0x60, ttl 64, id 47375, offset 0, flags [DF], proto TCP (6), length 40)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [F.], cksum 0xa1f2 (incorrect -> 0xceab), seq 7578, ack 3859, win 289, length 0
1542582412.642051 IP (tos 0x0, ttl 49, id 23423, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [.], cksum 0xb8fd (correct), ack 7578, win 5840, length 0
1542582412.648111 IP (tos 0x0, ttl 49, id 23424, offset 0, flags [DF], proto TCP (6), length 77)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [P.], cksum 0x8cf7 (correct), seq 3859:3896, ack 7579, win 5840, length 37
1542582412.648167 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [R], cksum 0xbf88 (correct), seq 1873675065, win 0, length 0
1542582412.652236 IP (tos 0x0, ttl 49, id 23425, offset 0, flags [DF], proto TCP (6), length 40)
24.187.183.18.51151 > 45.79.164.187.ca-2: Flags [F.], cksum 0xb8d6 (correct), seq 3896, ack 7579, win 5840, length 0
1542582412.652278 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 40)
45.79.164.187.ca-2 > 24.187.183.18.51151: Flags [R], cksum 0xbf88 (correct), seq 1873675065, win 0, length 0If it’s a valid certificate why did you do any of this on the asterisk server. Again. Stop messing with root bundles on your server and your phone. You are over complicating this. Get a valid certificate and add it to certificate manager. Then assign it in asterisk sip settings. Then restart asterisk.
Now that you’ve modified the root bundle on your server and the phone you’ve made it infinitely more complex and almost impossible for you to connect. You need to reset everything.
Go and brush up on how to get a tls certificate to work for a website. I’m not trying to be mean here but you are way over your head if you are modifying the root bundles on the phone. It’s never that complex. The phones. All phones. Already have a root bundle that will recognize as valid certificate as valid. The concepts work the same as any internet browser. You do not need to update your browsers root bundle to every site you visit.
Freepbx specific guides for this process that our support manager wrote (@cosmicwombat) (the comments are from his manager (@dolesec) and should also be read)
https://wiki.freepbx.org/plugins/servlet/mobile#content/view/64946938
What you have to consider about the secure calling tutorial that my wonderful coworker @malcolmd wrote is that it’s largely centered around self signed certificates. Which if you don’t know what you are doing can really over complicate the whole thing.
Since freepbx allows one to use let’s encrypt and upload a FQDN base certificate it’s just easier to follow the guide from freepbx.
Ok – lets me start again then
well i am almost ready to throw in the towel on this
i just dont see it
I reset everything as you asked
this time i went with a letsencrypt certificate
setup freepbx exactly the way your guide shows
factory reset the phone
and still not dice
i have put in a ticket with Yealink – maybe they can help??
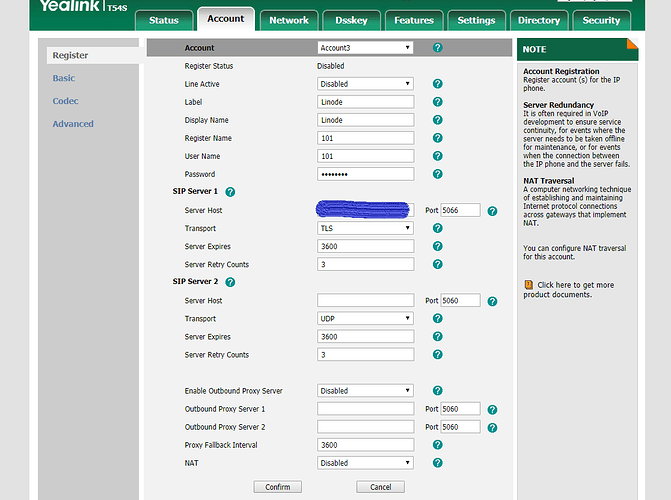
Show a screen shot of the account settings in the yealink.
Not likely.
Yealink wanted me to do all their testing. Nope.
http://forum.yealink.com/forum/showthread.php?mode=linear&tid=41194&pid=#pid
Related thread I made here.
I also had problems with the S series until one of the more recent firmware versions (66.83.0.35 or 66.83.0.50).
The G series will likely never work.
Quick question. Did you set this as the default cert?
Also, I remember reading somewhere, that a PBX reboot after installing the cert helped them. But I could be wrong on that.
Itzik
I did not set it as the default certificate – default is the default certificate
It would really help if you Enabled the account on the phone.
Very funny – i just turned it off after it failed so many times instead of leaving it on
Did also find this – wondering if this might be causing the SSL issues
Certificate chain is incomplete, missing intermediate(s)
Serial Number : 039DC39DD5BD27379D6FFB59F3BF220292AD
Signature Algorithm : Sha256 With RSA Encryption
Issuer Name : Let’s Encrypt
Common Name : xxx.xxx.com
Sans : xxx.xxx.com
Validity Period : November 18, 2018 to February 16, 2019
I wasn’t trying to be funny. I asked for the screenshots for your settings as to see why you weren’t seeing the requests at the PBX. I saw the account “Disabled” which would 100% be a reason as to why you could not see the requests, because there wouldn’t be any. I was offering a real solution.
And yes, this would be an issue. Pieces are missing.
I believe you have to set the LE cert as the default if you want it to work…
Not really as each place that needs a cert allows you to select a cert. The PBX creates a “default” self-signed cert during install, however, setting a cert to default just means “use this as the cert in places where I would be asked to use/select a cert”
Make sure that the Asterisk SIP Settings are pointed to the correct cert for both drivers.
I went into Certificate Management and clicked on edit for the LE cert and then chose update cert and now the certificate chain looks good
One problem solved –