Hi Guys,
Any one can help to mitigate this security issues we found?
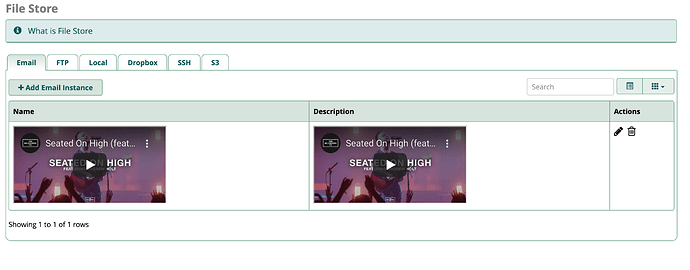
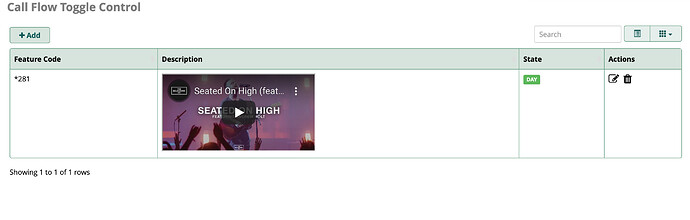
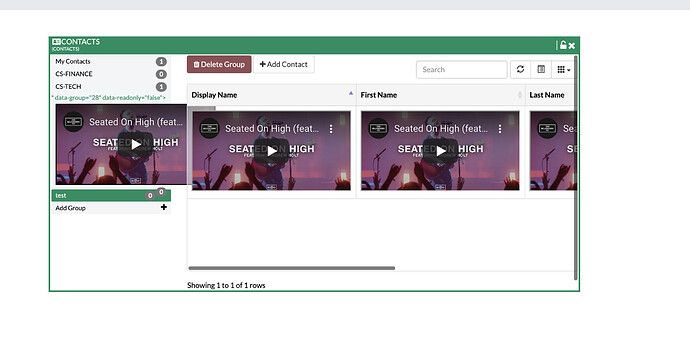
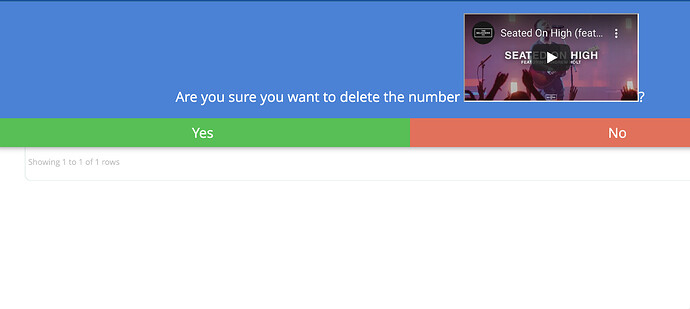
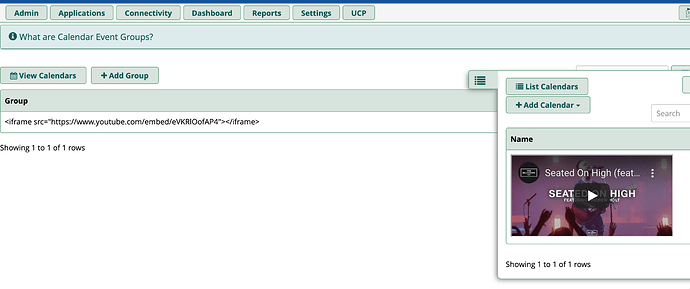
We performed security testing on FreePBX 15.0.23 and found out that the following modules are not filtering the inputs and allowing HTML tags/ XSS script to load. See below proof:
- Allow List
- Black List
- Contact Manager
- Calendar
- Calendar Events Groups
- Call Flow Toggle Control
- File Store
- UCP Contacts
Here are the HTML tags that I’ve input in every forms:
Also, script tags or other html tags could lead to broke the forms/ redirect you to other website.
Be careful not to run them on your production server. You have to delete the entry on the backend or database before it gets back to work.