Can you get into it via SSH to confirm anything?
I am able to ssh into mine, it does have the admin interface open (https), but asterisk and web are down on the system.
I have the same
So anyone finding this needs to do the following and provide the output. This file is an indicator your system has been compromised.
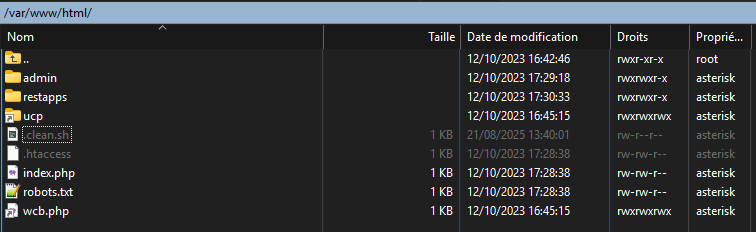
ls -l --time=ctime /var/www/html/.clean.sh
stat /var/www/html/.clean.sh
Check for other hidden files:
find /var/www/html -type f -name ".*.sh" -o -name ".*.php"
Check for it being in cron jobs
crontab -l
grep -R ".clean.sh" /etc/cron* /var/spool/cron /etc/systemd
@tcnetw0rks Do you have this file as well in /var/www/html?
stat /var/www/html/.clean.sh
File: ‘/var/www/html/.clean.sh’
Size: 732 Blocks: 8 IO Block: 4096 regular file
Device: fd00h/64768d Inode: 205442455 Links: 1
Access: (0664/-rw-rw-r--) Uid: ( 999/asterisk) Gid: ( 1000/asterisk)
Access: 2025-08-26 17:11:09.336376963 +0200
Modify: 2025-08-21 14:05:40.234566539 +0200
Change: 2025-08-26 17:09:31.023008447 +0200
find /var/www/html -type f -name ".*.sh" -o -name ".*.php"
/var/www/html/admin/modules/recording_report/vendor/php-ffmpeg/php-ffmpeg/.sami.php
/var/www/html/.clean.sh
[root@sbc3 ~]# crontab -l
[root@sbc3 ~]# grep -R ".clean.sh" /etc/cron* /var/spool/cron /etc/systemd
grep: /etc/systemd/system/multi-user.target.wants/cleanup-helper.service: No such file or directory
[root@TSEWDRY NEW PBX]# crontab -l
[root@TSEWDRY NEW PBX]# grep -R “.clean.sh” /etc/cron* /var/spool/cron /etc/systemd
grep: /etc/systemd/system/multi-user.target.wants/cleanup-helper.service: No such file or directory
[root@TSEWDRY NEW PBX]# ls -l --time=ctime /var/www/html/.clean.sh
-rw-r–r-- 1 asterisk asterisk 732 Aug 21 09:49 /var/www/html/.clean.sh
[root@TSEWDRY NEW PBX]# stat /var/www/html/.clean.sh
File: ‘/var/www/html/.clean.sh’
Size: 732 Blocks: 8 IO Block: 4096 regular file
Device: fd00h/64768d Inode: 52146496 Links: 1
Access: (0644/-rw-r–r–) Uid: ( 999/asterisk) Gid: ( 1000/asterisk)
Access: 2025-08-26 11:19:18.327632129 -0400
Modify: 2025-08-21 09:49:13.262805751 -0400
Change: 2025-08-21 09:49:13.262805751 -0400
Birth: -
This doesn’t smell good…
=== /var/www (webroot) ===
2025-08-21 14:05:40.2345665390 /var/www/html/.clean.sh
=== /var/log ===
=== /etc (configs) ===
2025-08-21 14:05:39.6335477570 /etc/freepbx.conf
Yeah, you’ve been compromised. You should also run: ps aux | grep -E "xmrig|minerd|cryptonight" because .clean.sh is what cleans up the crime scene after the crime has been committed.
nothing there…
[root@TSEWDRY NEW PBX]# ps aux | grep -E “xmrig|minerd|cryptonight”
root 20586 0.0 0.0 112808 980 pts/0 S+ 11:54 0:00 grep --color=auto -E xmrig|minerd|cryptonight
What we can see in the logs (August 21, 2025 ~14:05 Zurich time):
- Webshell execution: multiple POSTs on
/modular.phpreturning 200 — typical of a dropper/shell upload. - Creation/use of a second malicious script: first
/cache/monitor.phpreturns 404, then right after 200 (appears then executes). - Local backdoor attempt: a PHP script calls
http://127.0.0.1:32764/backend.phpfrom/var/www/html/cache/monitor.php(failed here, but that’s a clear implant signature). - 500 errors on the admin AJAX in the same timeframe (likely side-effects from modifications/injections).
- Very active external IP:
195.123.233.116hitting the admin and callingmodular.php/cache/monitor.phpdirectly (old Chrome/96 user-agent, distinct from your client Chrome/139 over IPv6) — consistent with session takeover or direct exploitation. - Burst of “localhost → /admin/ajax.php?module=zulu…” calls at the same moment; unusual volume, more consistent with a host-side script than normal user activity.
Short conclusion:
Confirmed compromise (modular.php webshell → monitor.php + attempted backend.php backdoor on local port). The 500 errors and Symfony exceptions you see are most likely consequences (modified vendor files, tampered permissions, autoload corruption).
Those are just some of the things that could employ this cleanup script. Your system was compromised on the 21st and it last ran that cleanup today. In fact, they ran the clean on your system roughly 40 minutes ago.
These are actively compromised systems. This is mostly likely an RCE over the web stack so the next really important question is:
How much exposure to the Internet do these systems have?
I’ve moved this to the Security section. Mods do not hide this we need to collect information.
We’ve collected the information we need and are working on a fix. Please see Security Advisory: Please Lock Down Your Administrator Access
I confirm this is probably what also happened to us…
This Instance is in the USA if that’s relevant.
No AMI access from Internet, only localhost.
root login disabled, ssh keys on created users and ssh.
FreePBX firewall and intrusion was on.
Is the FreePBX admin panel open to the Internet?
Yes it is.
I see almost identical hits in the web logs as @wifx
Since mine is a seldom-used home system, I’m going to block all internet access to it for now and probably just shut it down until I can get to reload it.
Why is it just open to the Internet?
Unless you want to setup a honeypot and see the realtime feed of exploits, this is definitely a risky move!