In my opinion I can use some advise on my firewall settings.
Freepbx GUI on non standard port (example 22934)
Letsencrypt port default port 80
Firewall settings
sudo iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
fail2ban-PBX-GUI all – 0.0.0.0/0 0.0.0.0/0
fail2ban-SSH tcp – 0.0.0.0/0 0.0.0.0/0 multiport dports 22
fail2ban-apache-auth all – 0.0.0.0/0 0.0.0.0/0
fail2ban-FTP tcp – 0.0.0.0/0 0.0.0.0/0 multiport dports 21
fail2ban-BadBots tcp – 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
fail2ban-api tcp – 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
fail2ban-recidive all – 0.0.0.0/0 0.0.0.0/0
fail2ban-SIP all – 0.0.0.0/0 0.0.0.0/0
fpbxfirewall all – 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain fail2ban-BadBots (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-FTP (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-PBX-GUI (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-SIP (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-SSH (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-apache-auth (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-api (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fail2ban-recidive (1 references)
target prot opt source destination
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain fpbx-rtp (1 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpts:16500:16512
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpts:4000:4999
Chain fpbxattacker (6 references)
target prot opt source destination
_ all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: ATTACKER side: source mask: 255.255.255.255_
DROP all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxblacklist (1 references)
target prot opt source destination
Chain fpbxchecktempwhitelist (1 references)
target prot opt source destination
fpbxtempwhitelist all – 0.0.0.0/0 0.0.0.0/0 ! recent: CHECK name: REPEAT side: source mask: 255.255.255.255
Chain fpbxfirewall (1 references)
target prot opt source destination
ACCEPT all – 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 connmark match ! 0x20 state RELATED,ESTABLISHED
ACCEPT icmp – 0.0.0.0/0 0.0.0.0/0
ACCEPT all – 0.0.0.0/0 255.255.255.255
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 PKTTYPE = multicast
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp spts:67:68 dpts:67:68
fpbx-rtp all – 0.0.0.0/0 0.0.0.0/0
fpbxblacklist all – 0.0.0.0/0 0.0.0.0/0
fpbxsignalling all – 0.0.0.0/0 0.0.0.0/0
fpbxsmarthosts all – 0.0.0.0/0 0.0.0.0/0
fpbxregistrations all – 0.0.0.0/0 0.0.0.0/0
fpbxnets all – 0.0.0.0/0 0.0.0.0/0
fpbxhosts all – 0.0.0.0/0 0.0.0.0/0
fpbxinterfaces all – 0.0.0.0/0 0.0.0.0/0
fpbxreject all – 0.0.0.0/0 0.0.0.0/0
fpbxrfw all – 0.0.0.0/0 0.0.0.0/0 mark match 0x2/0x2
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
lefilter tcp – 0.0.0.0/0 0.0.0.0/0 match-set lefilter dst
fpbxlogdrop all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxhosts (1 references)
target prot opt source destination
zone-trusted all – 66.133.109.36 0.0.0.0/0
zone-trusted all – 64.78.149.164 0.0.0.0/0
zone-trusted all – 199.102.239.170 0.0.0.0/0
zone-trusted all – 127.0.0.1 0.0.0.0/0
Chain fpbxinterfaces (1 references)
target prot opt source destination
zone-internal all – 0.0.0.0/0 0.0.0.0/0
zone-trusted all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxknownreg (4 references)
target prot opt source destination
_ all – 0.0.0.0/0 0.0.0.0/0 recent: REMOVE name: REPEAT side: source mask: 255.255.255.255_
_ all – 0.0.0.0/0 0.0.0.0/0 recent: REMOVE name: ATTACKER side: source mask: 255.255.255.255_
_ all – 0.0.0.0/0 0.0.0.0/0 recent: REMOVE name: TEMPWHITELIST side: source mask: 255.255.255.255_
_ all – 0.0.0.0/0 0.0.0.0/0 recent: REMOVE name: WHITELIST side: source mask: 255.255.255.255_
MARK all – 0.0.0.0/0 0.0.0.0/0 MARK or 0x4
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 mark match 0x1/0x1
fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-zulu all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-restapps all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-restapps_ssl all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-api all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-api_ssl all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxlogdrop (1 references)
target prot opt source destination
DROP all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxnets (1 references)
target prot opt source destination
zone-trusted all – 192.168.1.200 0.0.0.0/0
zone-trusted all – 192.168.1.217 0.0.0.0/0
zone-trusted all – 192.168.1.237 0.0.0.0/0
zone-trusted all – 192.168.1.218 0.0.0.0/0
zone-trusted all – 192.168.1.0/24 0.0.0.0/0
zone-trusted all – 192.168.0.0/16 0.0.0.0/0
zone-trusted all – 172.16.0.0/12 0.0.0.0/0
zone-trusted all – 10.0.0.0/8 0.0.0.0/0
Chain fpbxratelimit (1 references)
target prot opt source destination
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 mark match 0x4/0x4
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 90 hit_count: 1 name: WHITELIST side: source mask: 255.255.255.255
_ all – 0.0.0.0/0 0.0.0.0/0 state NEW recent: SET name: REPEAT side: source mask: 255.255.255.255_
_ all – 0.0.0.0/0 0.0.0.0/0 state NEW recent: SET name: DISCOVERED side: source mask: 255.255.255.255_
LOG all – 0.0.0.0/0 0.0.0.0/0 LOG flags 0 level 4
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 1 name: ATTACKER side: source mask: 255.255.255.255
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 200 name: REPEAT side: source mask: 255.255.255.255
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 300 hit_count: 100 name: REPEAT side: source mask: 255.255.255.255
fpbxshortblock all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 60 hit_count: 50 name: REPEAT side: source mask: 255.255.255.255
ACCEPT all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxregistrations (1 references)
target prot opt source destination
fpbxknownreg all – 7.x.x.x 0.0.0.0/0
fpbxknownreg all – 2x.x.x.x 0.0.0.0/0
fpbxknownreg all – 7x.x.x.x 0.0.0.0/0
fpbxknownreg all – 7x.x.x.x 0.0.0.0/0
Chain fpbxreject (1 references)
target prot opt source destination
rejsvc-xmpp all – 0.0.0.0/0 0.0.0.0/0
rejsvc-ftp all – 0.0.0.0/0 0.0.0.0/0
rejsvc-tftp all – 0.0.0.0/0 0.0.0.0/0
rejsvc-nfs all – 0.0.0.0/0 0.0.0.0/0
rejsvc-smb all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxrfw (1 references)
target prot opt source destination
_ all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: DISCOVERED side: source mask: 255.255.255.255_
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 90 hit_count: 1 name: WHITELIST side: source mask: 255.255.255.255
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 90 hit_count: 1 name: TEMPWHITELIST side: source mask: 255.255.255.255
fpbxchecktempwhitelist all – 0.0.0.0/0 0.0.0.0/0 ! recent: CHECK seconds: 86400 name: TEMPWHITELIST side: source mask: 255.255.255.255
_ all – 0.0.0.0/0 0.0.0.0/0 recent: REMOVE name: TEMPWHITELIST side: source mask: 255.255.255.255_
_ all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: REPEAT side: source mask: 255.255.255.255_
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 10 hit_count: 50 name: REPEAT side: source mask: 255.255.255.255
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 1 name: ATTACKER side: source mask: 255.255.255.255
fpbxshortblock all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 60 hit_count: 10 name: SIGNALLING side: source mask: 255.255.255.255
_ all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: SIGNALLING side: source mask: 255.255.255.255_
fpbxattacker all – 0.0.0.0/0 0.0.0.0/0 recent: CHECK seconds: 86400 hit_count: 100 name: REPEAT side: source mask: 255.255.255.255
ACCEPT all – 0.0.0.0/0 0.0.0.0/0
Chain fpbxshortblock (2 references)
target prot opt source destination
_ all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: CLAMPED side: source mask: 255.255.255.255_
REJECT all – 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
Chain fpbxsignalling (1 references)
target prot opt source destination
MARK udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:6xxx MARK set 0x1
MARK udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5xxx MARK set 0x1
MARK tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:6xxx MARK set 0x1
Chain fpbxsmarthosts (1 references)
target prot opt source destination
ACCEPT all – 7x.x.x.x 0.0.0.0/0 mark match 0x1/0x1
ACCEPT all – 7x.x.x.x 0.0.0.0/0 mark match 0x1/0x1
Chain fpbxsvc-api (2 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:83
Chain fpbxsvc-api_ssl (2 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:2443
Chain fpbxsvc-chansip (1 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:6xxx
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:6xxx
Chain fpbxsvc-ftp (0 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:21
Chain fpbxsvc-http (1 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
Chain fpbxsvc-https (1 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
Chain fpbxsvc-iax (1 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:xxxx
Chain fpbxsvc-isymphony (0 references)
target prot opt source destination
Chain fpbxsvc-letsencrypt (0 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain fpbxsvc-nfs (0 references)
target prot opt source destination
Chain fpbxsvc-ntp (1 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:123
Chain fpbxsvc-pjsip (1 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:5160
Chain fpbxsvc-provis (3 references)
target prot opt source destination
fpbxratelimit tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:84
Chain fpbxsvc-provis_ssl (3 references)
target prot opt source destination
Chain fpbxsvc-restapps (2 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:82
Chain fpbxsvc-restapps_ssl (2 references)
target prot opt source destination
Chain fpbxsvc-smb (0 references)
target prot opt source destination
Chain fpbxsvc-ssh (1 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
Chain fpbxsvc-tftp (0 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:69
Chain fpbxsvc-ucp (4 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxxx
Chain fpbxsvc-vpn (3 references)
target prot opt source destination
ACCEPT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:1194
Chain fpbxsvc-webrtc (1 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:xxxx
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:8089
Chain fpbxsvc-xmpp (0 references)
target prot opt source destination
ACCEPT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:5222
Chain fpbxsvc-zulu (1 references)
target prot opt source destination
Chain fpbxtempwhitelist (1 references)
target prot opt source destination
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 recent: SET name: TEMPWHITELIST side: source mask: 255.255.255.255
Chain lefilter (1 references)
target prot opt source destination
CONNMARK all – 0.0.0.0/0 0.0.0.0/0 state NEW CONNMARK set 0x20
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 state NEW
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 STRING match “GET /.well-known/acme-challenge/” ALGO name kmp FROM 52 TO 53
ACCEPT all – 0.0.0.0/0 0.0.0.0/0 STRING match “GET /.freepbx-known/” ALGO name kmp FROM 52 TO 53
RETURN all – 0.0.0.0/0 0.0.0.0/0
Chain rejsvc-ftp (1 references)
target prot opt source destination
REJECT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:21 reject-with icmp-port-unreachable
Chain rejsvc-nfs (1 references)
target prot opt source destination
Chain rejsvc-smb (1 references)
target prot opt source destination
Chain rejsvc-tftp (1 references)
target prot opt source destination
REJECT udp – 0.0.0.0/0 0.0.0.0/0 udp dpt:69 reject-with icmp-port-unreachable
Chain rejsvc-xmpp (1 references)
target prot opt source destination
REJECT tcp – 0.0.0.0/0 0.0.0.0/0 tcp dpt:5222 reject-with icmp-port-unreachable
Chain zone-external (0 references)
target prot opt source destination
MARK all – 0.0.0.0/0 0.0.0.0/0 MARK or 0x10
fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
Chain zone-internal (1 references)
target prot opt source destination
MARK all – 0.0.0.0/0 0.0.0.0/0 MARK or 0x4
fpbxsvc-ssh all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-http all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-https all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-pjsip all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-chansip all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-iax all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-webrtc all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-api all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-api_ssl all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-ntp all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-restapps all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-restapps_ssl all – 0.0.0.0/0 0.0.0.0/0
Chain zone-other (0 references)
target prot opt source destination
MARK all – 0.0.0.0/0 0.0.0.0/0 MARK or 0x8
fpbxsvc-ucp all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-provis_ssl all – 0.0.0.0/0 0.0.0.0/0
fpbxsvc-vpn all – 0.0.0.0/0 0.0.0.0/0
Chain zone-trusted (13 references)
target prot opt source destination
ACCEPT all – 0.0.0.0/0 0.0.0.0/0
ONLY WHEN MY FIREWALL is turned off
Firewall temp off.
fwconsole cert --updateall --force
Forced update enabled !!!
Processing: mine.fqdn.com, Local IP: 2x.x.x.x, Public IP: 2x.x.x.x
Self test: trying fqdn.com - This website is for sale! - fqdn Resources and Information.
Self test: received e52ef79218253aa5d81c73ab7f5ffdab
Getting list of URLs for API
Requesting new nonce for client communication
Account already registered. Continuing.
Sending registration to letsencrypt server
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/new-acct
Account: https://acme-v02.api.letsencrypt.org/acme/acct/27707545
Starting certificate generation process for domains
Requesting challenge for mine.fqdn.com
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/new-order
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/authz-v3/33755902140
Got challenge token for mine.fqdn.com
Token for mine.fqdn.com saved at /var/www/html/.well-known/acme-challenge/O-6XBc_sYJLAsJwVfgiyFtDj_iW5Ane1UuW6tP8or-4 and should be available at fqdn.com - This website is for sale! - fqdn Resources and Information.
Sending request to challenge
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/33755902140/4KRT7Q
Verification pending, sleeping 1s
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/chall-v3/33755902140/4KRT7Q
Verification ended with status: valid
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/finalize/27707545/27556314100
Sending signed request to https://acme-v02.api.letsencrypt.org/acme/cert/0464686c23ba0d621988432d9e1e9ef2dfd1
Got certificate! YAY!
Saving fullchain.pem
Saving cert.pem
Saving chain.pem
Done !!§§!
Successfully updated certificate named “mine.fqdn.com”
I’m already happy that I can overcome the renewal issue via this temporarily workaround, but my goal is an automatic renewal in FreePBX. In my opinion it is a firewall issue, but I can use some help finding / resolving this issue
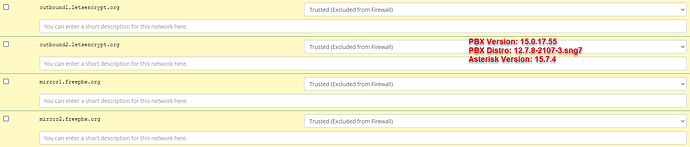
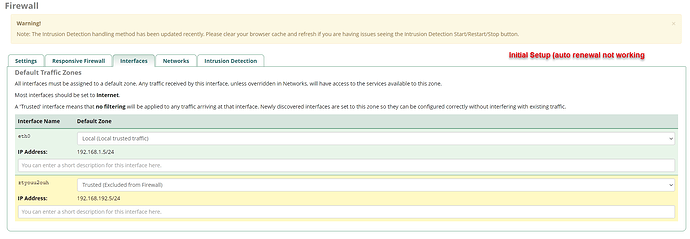
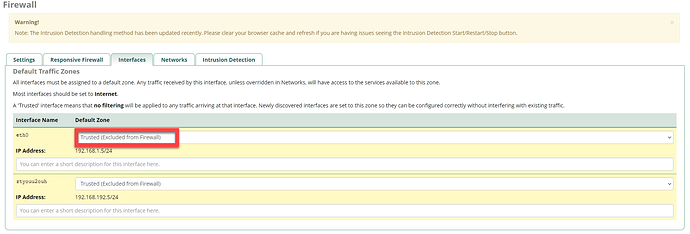
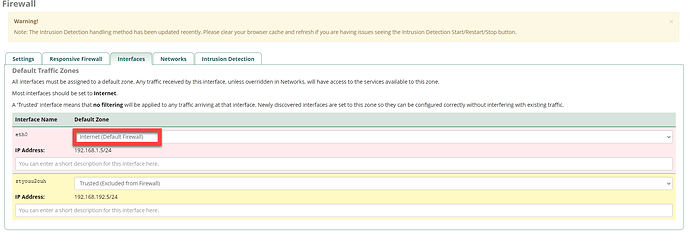
 . I don’t easily touch firewalls, because there is a reason to have a firewall in place. Nevertheless, hopefully it helps others in a similar situation.
. I don’t easily touch firewalls, because there is a reason to have a firewall in place. Nevertheless, hopefully it helps others in a similar situation.