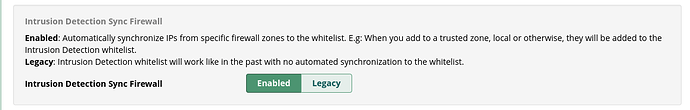
Having an issue with the new firewall? IP’s that are on the whitelist are getting banned? I have had 2 PBX’s now that have banned an IP that was on the whitelist? Both happened today and I have been running this config option about 3 weeks. I thought IP’s on the white list couldnt get banned??
There is both an Intrusion Detection whitelist and the Trusted zone in Networks (not called ‘whitelist’ but that’s what it is).
An address must be listed in both places to ensure that its errors will not cause it to be banned.
An issue that this new approach reintroduced, at least for me, is that if you are using iptables and fail2ban manually, the reload hooks wipe out all the manual configuration. Since intrusion detection will now not work without the firewall module at least installed, now I can’t use manually defined rules. I tried looking when the iptables rules are deleted, but can’t find it on my own.
I opened a bug report when this first started, a couple years ago, and the solution at that time was to check against the md5 hash of the default iptables rules file and don’t delete it if the hash was different. Maybe this new situation is somehow related to that? The md5 hash check is still present on sysadmin hooks but somehow the manual rules get wiped out if the firewall module is installed with the firewall itself being disabled.
There’s an entire tab of the GUI dedicated to letting you do custom rules
Example:
I saw that, but I want to manage my own rules on my own way, without the need to enable the firewall module, just like I was able to do before the update. I just don’t understand why I’m being forced again into using the firewall module if I want to manage my own rules.
Perhaps you should disable that module than ?
The issue with disabling the module is that it completely disables fail2ban. That was not the case with the previous firewall module.
Then if you have disabled the module and it completely disables fail2ban , perhaps you should start fail2ban under your own initiative because , well , you can!
(The current distro comes completes with one of those new systemd service file’s )
Enable the module but keep firewall disabled.
If you did that, what would iptables be left with?
When I do that, either the sysadmin hooks or the firewall hooks, not sure which ones, are deleting my custom rules.
Any “custom” rule would need to be -I inserted (not -A added) before any rule that would pre-empt them and should be honored as a pre-dependency of any service that wants to control iptables at the system level.
I hear you, but something that was working before the firewall was revamped, is not working anymore. I have my iptables rules saved. If I disable the firewall but leave the module installed so I can use intrusion detection, then my saved rules are not honored. If I uninstall the firewall module completely, then intrusion detection stops working.
“Intrusion Detection” is an alias for fail2ban, it has always worked fine all on it’s own, take the opportunity to get the latest and greatest from them and just use systemctl at the system level.
It is not a good firewall in itself but appending it to the set of rules you are happy with can but improve your “IDS” ( Please be aware that it does a whole Sh*?-load more than just SIP, configure, enable and use them jails !)
Hello @dvsatech,
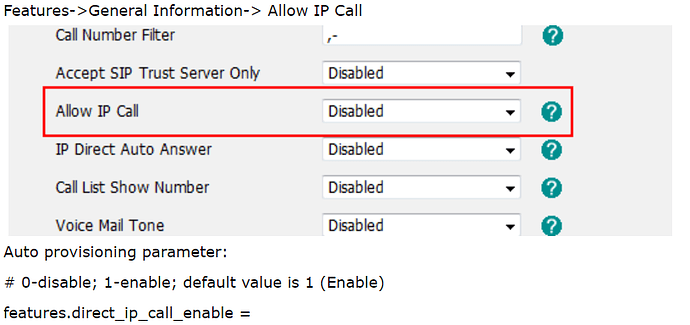
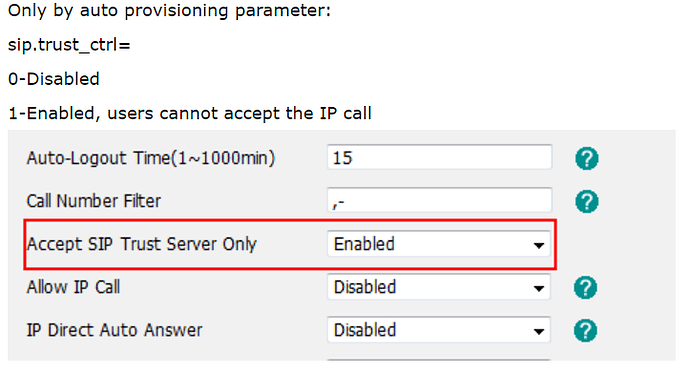
To disable the SIP attacks on your IP phones (usually a direct scan of sipvicius or a similar tool), enable a setting on your IP phone to accept SIP invites only from a known source like your PBX, and disable a direct IP call on the phone.
This is an example from a Yealink phone:
You can take a look at this manual as well for other brands of IP phones:
Thank you,
Daniel Friedman
Trixton LTD.
This topic was automatically closed 31 days after the last reply. New replies are no longer allowed.