http is also insecure. https authentication deemed absolutely essential, but even then https connections ‘leak’ critical info without SNI verification before forwarding to the provisioning server.
Noisy? Yes. Insecure? No.
Can sshd be configured insecurely? Yes.
As I posted, if you
- denied root login
- denied password logins
Then you are still noisy but secure. it would assume public key logins, unless you leak your cert. If 2 then you don’t need 1, I like quiet and secure. If you are hyper paranoid then you can PAM rotate and more such . . .
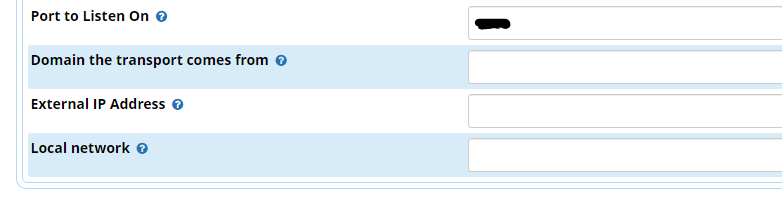
Thanks for the help here. In context Freepbx GUI this refers to Port To Listen On, Domain the transport comes from in Asterisk SIP Settings?
This system is not in a domain.
It will behoove you to get a domain, either real or by dynamic dns, That way incoming connections will only pass muster if they are directed to that domain and you tell the client to register against such domain and not an IP address, even the dynamic DNS IP will generally be quite stable as to what the ip address is.
Meaning the SIP Server value changes to host.domain.com rather than the IP xxx.xxx.xxx.xxx
A caller would be [email protected] and having Domain the transport comes from means any callers not @host.domain.com are rejected. Correct?
Implementing a domain for this box immediately.
correct
If using chan_sip add to /etc/asterisk/sip_general_custom.conf
domain=your.domain.com
domain=127.0.0.1
if using chan_pjsip, as you noted
current versions of fail2ban should capture the bad guys
Returning to a previous comment. My CDR reports for the pirate calls show Return in the App column. Legit calls have Dial in the App column. What does Return mean?
the last application that ran was a return from a macro or gosub, the cel records should show from what
This topic was automatically closed 7 days after the last reply. New replies are no longer allowed.