Hi All,
I’m pretty sure of what I’m looking at, but wanted to run it by you all.
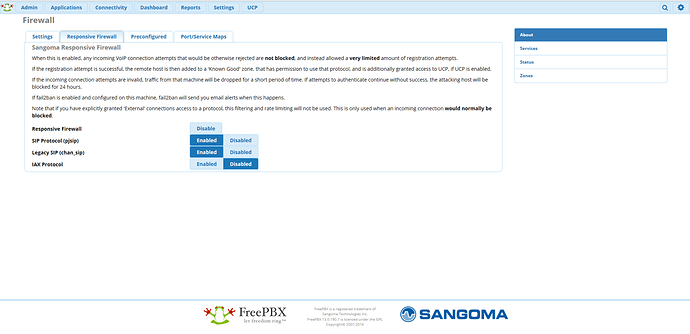
In the Reports menu > Asterisk Log Files - the log named “Full” I have found several huge sections that look like this
[2016-12-09 20:16:12] NOTICE[12561] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“9999” sip:[email protected]’ failed for ‘131.153.5.226:5071’ (callid: 182ae8b6475a57bd4663974b8c18da55) - No matching endpoint found
[2016-12-09 20:16:22] NOTICE[1811] chan_sip.c: Received SIP subscribe for peer without mailbox: 1943
[2016-12-09 20:17:19] NOTICE[12655] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“9999” sip:[email protected]’ failed for ‘131.153.5.226:5070’ (callid: 98d55f274ad6de49d4a9d690b6f7476f) - No matching endpoint found
[2016-12-09 20:17:55] NOTICE[1811] chan_sip.c: Received SIP subscribe for peer without mailbox: 4443
[2016-12-09 20:18:05] NOTICE[12655] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“101” sip:[email protected]’ failed for ‘162.254.207.67:5070’ (callid: 1b5add5706f97a00a179e9a501eb4938) - No matching endpoint found
[2016-12-09 20:18:24] NOTICE[12655] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“9999” sip:[email protected]’ failed for ‘131.153.5.226:5074’ (callid: b28ebd3d3d63052616495dc0d0075fe3) - No matching endpoint found
[2016-12-09 20:19:22] NOTICE[1811] chan_sip.c: Received SIP subscribe for peer without mailbox: 1943
[2016-12-09 20:19:32] NOTICE[12857] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“9999” sip:[email protected]’ failed for ‘131.153.5.226:5078’ (callid: 9af8747762b8edb70b5a9061df691506) - No matching endpoint found
[2016-12-09 20:20:18] NOTICE[12857] res_pjsip/pjsip_distributor.c: Request ‘INVITE’ from ‘“2200” sip:[email protected]’ failed for ‘69.64.57.15:5071’ (callid: 41f550858f0c4ebf4630df7c9380c6cb) - No matching endpoint found
The list that I have prepared wouldn’t really be nice in this post due to it’s size so, I’ve just put up a snippet. I was looking for the like code quote option in the editor but either I cant find it or the dev here didn’t think it was important. So there’s the short snippet in blockquote.
Now, I’ve also seen in the fail2ban log file many of the same unknown IP addresses. So, I’m thinking that the server is being hit by an attacker and as should be the attacker IP is blocked. Correct?
Thanks,
John