I recently setup a freepbx firewall for a client. I changed the default Asterisk bind port to reduce the risk of hacking. I setup the firewall and set the eth0 interface as External and Enabled the Responsive firewall because on occassion client requires remote access via softphone to the PBX.
All seemed fine until just recently when he travelled to a new destination and couldn’t connect. I began to investigate (I added my IP to trusted zone so i could get in). I realised that even the sip trunks from External DID providers were unreachable. I determined that the firewall was still referencing port 5060 as the signalling port for Chan_sip even though i had updated the bind port in Freepbx interface. I was able to restore access by adding a custom service using the new bind port and setting it up as part of the “External” zone. This I know is not safe as it is unprotected by the firewall. How do I update the chan_sip port in the Firewall? Any help is much appreciated
It updates automatically. What version of Firewall and Sip Settings are you running?
FreePBX 13.0.123
Firewall 13.0.33
Asterisk SIP Settings 13.0.23.2
I thought so too and this seems to just have happened recently.
That’s the latest, and (should be) bug-free version. So what makes you think it’s listening on the wrong port?
Can you paste the output of ‘iptables-save’? You should also see the ports it’s using in the ‘Services’ window. To paste into discourse, put three backticks - ``` on a blank line, then the paste, then three more backticks. Like this.
```
This is a multi Line
quotation with text
```
That ends up like this:
This is a multi Line
quotation with text
[root@localhost ~]# iptables-save
# Generated by iptables-save v1.4.7 on Tue May 31 09:45:13 2016
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [9979:2687653]
:fail2ban-BadBots - [0:0]
:fail2ban-FTP - [0:0]
:fail2ban-SIP - [0:0]
:fail2ban-SSH - [0:0]
:fail2ban-apache-auth - [0:0]
:fail2ban-recidive - [0:0]
:fpbx-rtp - [0:0]
:fpbxattacker - [0:0]
:fpbxblacklist - [0:0]
:fpbxfirewall - [0:0]
:fpbxhosts - [0:0]
:fpbxinterfaces - [0:0]
:fpbxknownreg - [0:0]
:fpbxlogdrop - [0:0]
:fpbxnets - [0:0]
:fpbxregistrations - [0:0]
:fpbxreject - [0:0]
:fpbxrfw - [0:0]
:fpbxshortblock - [0:0]
:fpbxsignalling - [0:0]
:fpbxsmarthosts - [0:0]
:fpbxsvc-5f7d3d2e36ce487f - [0:0]
:fpbxsvc-chansip - [0:0]
:fpbxsvc-ftp - [0:0]
:fpbxsvc-http - [0:0]
:fpbxsvc-https - [0:0]
:fpbxsvc-iax - [0:0]
:fpbxsvc-isymphony - [0:0]
:fpbxsvc-nfs - [0:0]
:fpbxsvc-pjsip - [0:0]
:fpbxsvc-provis - [0:0]
:fpbxsvc-restapps - [0:0]
:fpbxsvc-smb - [0:0]
:fpbxsvc-ssh - [0:0]
:fpbxsvc-tftp - [0:0]
:fpbxsvc-ucp - [0:0]
:fpbxsvc-vpn - [0:0]
:fpbxsvc-webrtc - [0:0]
:fpbxsvc-xmpp - [0:0]
:fpbxsvc-zulu - [0:0]
:rejsvc-nfs - [0:0]
:rejsvc-smb - [0:0]
:rejsvc-webrtc - [0:0]
:zone-external - [0:0]
:zone-internal - [0:0]
:zone-other - [0:0]
:zone-trusted - [0:0]
-A INPUT -p tcp -m multiport --dports 21 -j fail2ban-FTP
-A INPUT -p tcp -m multiport --dports 80 -j fail2ban-apache-auth
-A INPUT -j fail2ban-SIP
-A INPUT -p tcp -m multiport --dports 80,443 -j fail2ban-BadBots
-A INPUT -p tcp -m multiport --dports 22 -j fail2ban-SSH
-A INPUT -j fail2ban-recidive
-A INPUT -j fpbxfirewall
-A fail2ban-BadBots -j RETURN
-A fail2ban-FTP -j RETURN
-A fail2ban-SIP -j RETURN
-A fail2ban-SSH -j RETURN
-A fail2ban-apache-auth -j RETURN
-A fail2ban-recidive -j RETURN
-A fpbx-rtp -p udp -m udp --dport 10000:20000 -j ACCEPT
-A fpbx-rtp -p udp -m udp --dport 4000:4999 -j ACCEPT
-A fpbxattacker -m recent --set --name ATTACKER --rsource
-A fpbxattacker -j LOG --log-prefix "attacker: "
-A fpbxattacker -j DROP
-A fpbxfirewall -i lo -j ACCEPT
-A fpbxfirewall -p tcp -m state --state RELATED,ESTABLISHED -j ACCEPT
-A fpbxfirewall -p udp -m udp --sport 1:1024 -m state --state RELATED,ESTABLISHED -j ACCEPT
-A fpbxfirewall -p icmp -j ACCEPT
-A fpbxfirewall -d 255.255.255.255/32 -j ACCEPT
-A fpbxfirewall -m pkttype --pkt-type multicast -j ACCEPT
-A fpbxfirewall -p udp -m udp --sport 67:68 --dport 67:68 -j ACCEPT
-A fpbxfirewall -j fpbx-rtp
-A fpbxfirewall -j fpbxblacklist
-A fpbxfirewall -j fpbxsignalling
-A fpbxfirewall -j fpbxsmarthosts
-A fpbxfirewall -j fpbxregistrations
-A fpbxfirewall -j fpbxnets
-A fpbxfirewall -j fpbxhosts
-A fpbxfirewall -j fpbxinterfaces
-A fpbxfirewall -j fpbxreject
-A fpbxfirewall -m mark --mark 0x2/0x2 -j fpbxrfw
-A fpbxfirewall -j fpbxlogdrop
-A fpbxhosts -s 127.0.0.1/32 -j zone-trusted
-A fpbxinterfaces -i eth0 -j zone-external
-A fpbxknownreg -m mark --mark 0x1/0x1 -j ACCEPT
-A fpbxknownreg -j fpbxsvc-ucp
-A fpbxknownreg -j fpbxsvc-zulu
-A fpbxlogdrop -j DROP
-A fpbxnets -s XX.XX.XX.XX/32 -j zone-trusted
-A fpbxnets -s XX.XX.XX.XX/32 -j zone-trusted
-A fpbxnets -s XX.XX.XX.XX/32 -j zone-trusted
-A fpbxnets -s 192.168.0.0/24 -j zone-trusted
-A fpbxnets -s XX.XX.XX.XX/16 -j zone-trusted
-A fpbxregistrations -s 192.168.0.7/32 -j fpbxknownreg
-A fpbxregistrations -s XX.XX.XX.74/32 -j fpbxknownreg
-A fpbxregistrations -s 37.157.54.196/32 -j fpbxknownreg
-A fpbxregistrations -s XX.XX.XX.XX/32 -j fpbxknownreg
-A fpbxregistrations -s XX.XX.XX.XX/32 -j fpbxknownreg
-A fpbxreject -j rejsvc-webrtc
-A fpbxreject -j rejsvc-nfs
-A fpbxreject -j rejsvc-smb
-A fpbxrfw -m recent --set --name REPEAT --rsource
-A fpbxrfw -m recent --set --name DISCOVERED --rsource
-A fpbxrfw -m recent --rcheck --seconds 10 --hitcount 50 --name REPEAT --rsource -j fpbxattacker
-A fpbxrfw -m recent --rcheck --seconds 86400 --hitcount 1 --name ATTACKER --rsource -j fpbxattacker
-A fpbxrfw -m recent --rcheck --seconds 60 --hitcount 10 --name SIGNALLING --rsource -j fpbxshortblock
-A fpbxrfw -m recent --set --name SIGNALLING --rsource
-A fpbxrfw -m recent --rcheck --seconds 86400 --hitcount 100 --name REPEAT --rsource -j fpbxattacker
-A fpbxrfw -j ACCEPT
-A fpbxshortblock -m recent --set --name CLAMPED --rsource
-A fpbxshortblock -j LOG --log-prefix "clamped: "
-A fpbxshortblock -j REJECT --reject-with icmp-port-unreachable
-A fpbxsignalling -p udp -m udp --dport 5060 -j MARK --set-xmark 0x3/0xffffffff
-A fpbxsmarthosts -s 185.45.152.174/32 -m mark --mark 0x1/0x1 -j ACCEPT
-A fpbxsmarthosts -s 37.157.54.197/32 -m mark --mark 0x1/0x1 -j ACCEPT
-A fpbxsmarthosts -s 37.157.54.196/32 -m mark --mark 0x1/0x1 -j ACCEPT
-A fpbxsmarthosts -s 37.157.54.194/32 -m mark --mark 0x1/0x1 -j ACCEPT
-A fpbxsvc-5f7d3d2e36ce487f -p udp -m udp --dport 25160 -j ACCEPT
-A fpbxsvc-chansip -p udp -m udp --dport 5060 -j ACCEPT
-A fpbxsvc-ftp -p tcp -m tcp --dport 21 -j ACCEPT
-A fpbxsvc-http -p tcp -m tcp --dport 80 -j ACCEPT
-A fpbxsvc-https -p tcp -m tcp --dport 443 -j ACCEPT
-A fpbxsvc-iax -p udp -m udp --dport 4569 -j ACCEPT
-A fpbxsvc-isymphony -p tcp -m tcp --dport 58080 -j ACCEPT
-A fpbxsvc-isymphony -p tcp -m tcp --dport 55050 -j ACCEPT
-A fpbxsvc-provis -p tcp -m tcp --dport 83 -j ACCEPT
-A fpbxsvc-restapps -p tcp -m tcp --dport 84 -j ACCEPT
-A fpbxsvc-ssh -p tcp -m tcp --dport 22 -j ACCEPT
-A fpbxsvc-tftp -p udp -m udp --dport 69 -j ACCEPT
-A fpbxsvc-ucp -p tcp -m tcp --dport 81 -j ACCEPT
-A fpbxsvc-ucp -p tcp -m tcp --dport 8001 -j ACCEPT
-A fpbxsvc-ucp -p tcp -m tcp --dport 8003 -j ACCEPT
-A fpbxsvc-vpn -p udp -m udp --dport 1194 -j ACCEPT
-A fpbxsvc-webrtc -p tcp -m tcp --dport 8088 -j ACCEPT
-A fpbxsvc-webrtc -p tcp -m tcp --dport 8089 -j ACCEPT
-A fpbxsvc-xmpp -p tcp -m tcp --dport 5222 -j ACCEPT
-A rejsvc-webrtc -p tcp -m tcp --dport 8088 -j REJECT --reject-with icmp-port-unreachable
-A rejsvc-webrtc -p tcp -m tcp --dport 8089 -j REJECT --reject-with icmp-port-unreachable
-A zone-external -j fpbxsvc-https
-A zone-external -j fpbxsvc-ucp
-A zone-external -j fpbxsvc-vpn
-A zone-external -j fpbxsvc-xmpp
-A zone-external -j fpbxsvc-5f7d3d2e36ce487f
-A zone-internal -j fpbxsvc-ssh
-A zone-internal -j fpbxsvc-http
-A zone-internal -j fpbxsvc-https
-A zone-internal -j fpbxsvc-ucp
-A zone-internal -j fpbxsvc-isymphony
-A zone-internal -j fpbxsvc-provis
-A zone-internal -j fpbxsvc-vpn
-A zone-internal -j fpbxsvc-restapps
-A zone-internal -j fpbxsvc-xmpp
-A zone-internal -j fpbxsvc-ftp
-A zone-internal -j fpbxsvc-tftp
-A zone-internal -j fpbxsvc-5f7d3d2e36ce487f
-A zone-other -j fpbxsvc-ucp
-A zone-other -j fpbxsvc-provis
-A zone-other -j fpbxsvc-vpn
-A zone-other -j fpbxsvc-xmpp
-A zone-trusted -j ACCEPT
COMMIT
# Completed on Tue May 31 09:45:13 2016
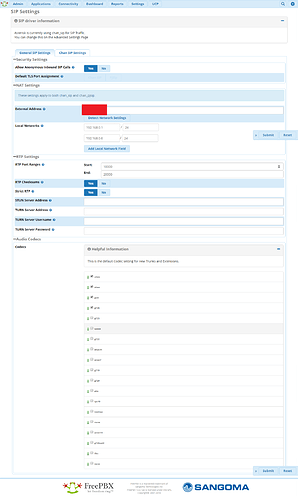
And yes It does say 5060 under services

You might want to check sip settings. It’s set to 5060 there.
Nope its set correctly to 25160 and phones are registering

Well that’s interesting. I’ll look into that tomorrow.
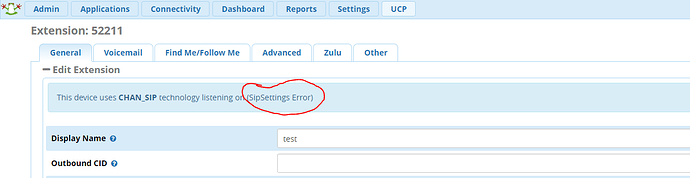
Hello, I just noticed this error under an extension. It appears something is wrong with Asterisk sip settings. I thought of reinstalling but the option to uninstall is not available in ‘module admin’
any suggestions.
Anything unusual in Settings, Asterisk SIP Settings?
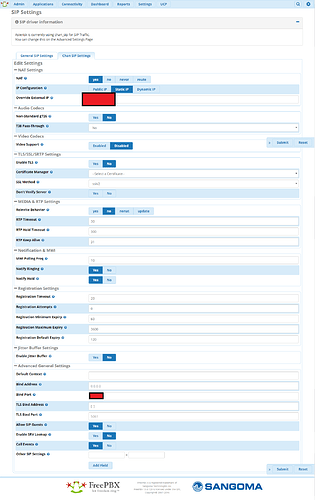
I was able to clear the error by enabling pjsip driver in Advanced Settings. It was set to chan_sip alone. but now with both drivers enabled the error is cleared. Firewall is also referencing correct chan_sip port (bind port). I’ll keep observing for now though. But Thanks everyone