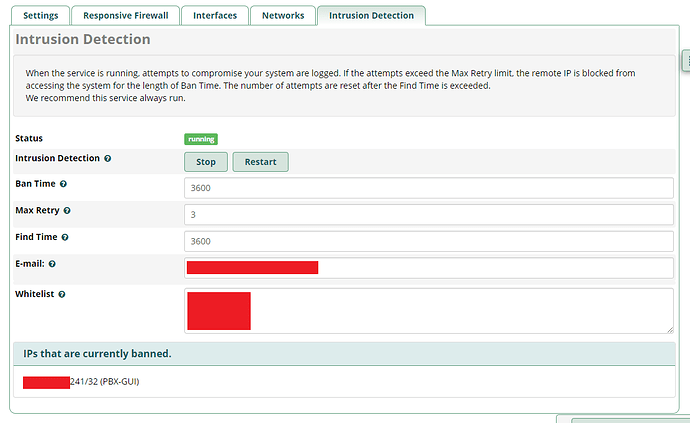
Let me preface this by saying there is no issue with fail2ban. fail2ban lists the banned IP address in JAIL as it should. I believe the problem is Apache webserver is not respecting the JAIL and is serving up HTTPS on port 443 regardless of what is in the JAIL.
With that said, here is the info you asked for;
I dont think jail.conf is what you want to see. Its default freepbx and its mostly all commented out.
# Fail2Ban jail specifications file
#
# Comments: use '#' for comment lines and ';' for inline comments
#
# Changes: in most of the cases you should not modify this
# file, but provide customizations in jail.local file, e.g.:
#
# [DEFAULT]
# bantime = 3600
#
# [ssh-iptables]
# enabled = true
#
# The DEFAULT allows a global definition of the options. They can be overridden
# in each jail afterwards.
[DEFAULT]
# "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not
# ban a host which matches an address in this list. Several addresses can be
# defined using space separator.
# "bantime" is the number of seconds that a host is banned.
bantime = 3600
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
findtime = 3600
# "maxretry" is the number of failures before a host get banned.
maxretry = 3
# "backend" specifies the backend used to get files modification.
# Available options are "pyinotify", "gamin", "polling" and "auto".
# This option can be overridden in each jail as well.
#
# pyinotify: requires pyinotify (a file alteration monitor) to be installed.
# If pyinotify is not installed, Fail2ban will use auto.
# gamin: requires Gamin (a file alteration monitor) to be installed.
# If Gamin is not installed, Fail2ban will use auto.
# polling: uses a polling algorithm which does not require external libraries.
# auto: will try to use the following backends, in order:
# pyinotify, gamin, polling.
backend = auto
# "usedns" specifies if jails should trust hostnames in logs,
# warn when reverse DNS lookups are performed, or ignore all hostnames in logs
#
# yes: if a hostname is encountered, a reverse DNS lookup will be performed.
# warn: if a hostname is encountered, a reverse DNS lookup will be performed,
# but it will be logged as a warning.
# no: if a hostname is encountered, will not be used for banning,
# but it will be logged as info.
usedns = warn
# This jail corresponds to the standard configuration in Fail2ban 0.6.
# The mail-whois action send a notification e-mail with a whois request
# in the body.
What I believe you want to see is jail.local (below), which is default freepbx, with no mods.
# Configuration automatically generated via the Sysadmin Module
# This file will be overwritten by Sysadmin on startup. If you modify
# this file, your changes will be lost. DO NOT MODIFY THIS FILE!
# generated: Sun, 15 Jan 2023 21:00:05 +0000
[DEFAULT]
ignoreip =
sendername = FreePBX Alerts
bantime = 3600
findtime = 3600
maxretry = 4
backend = auto
[asterisk-iptables]
enabled = true
filter = asterisk
action = iptables-allports[name=SIP, protocol=all]
sendmail[name=SIP, [email protected], [email protected]]
logpath = /var/log/asterisk/fail2ban
[pbx-gui]
enabled = true
filter = freepbx
action = iptables-allports[name=PBX-GUI, protocol=all]
sendmail[name=PBX-GUI, [email protected], [email protected]]
logpath = /var/log/asterisk/freepbx_security.log
[ssh-iptables]
enabled = true
filter = sshd
action = iptables-multiport[name=SSH, protocol=tcp, port=ssh]
sendmail[name=SSH, [email protected], [email protected]]
logpath = /var/log/secure
[apache-tcpwrapper]
enabled = true
filter = apache-auth
action = iptables-allports[name=apache-auth, protocol=all]
sendmail[name=apache-auth, [email protected], [email protected]]
logpath = /var/log/httpd/error_log
[vsftpd-iptables]
enabled = true
filter = vsftpd
action = iptables-multiport[name=FTP, protocol=tcp, port=ftp]
sendmail[name=FTP, [email protected], [email protected]]
logpath = /var/log/vsftpd.log
[apache-badbots]
enabled = true
filter = apache-badbots
action = iptables-multiport[name=BadBots, protocol=tcp, port="http,https"]
sendmail[name=BadBots, [email protected], [email protected]]
logpath = /var/log/httpd/*access_log
[apache-api]
enabled = true
filter = apache-api
action = iptables-multiport[name=api, protocol=tcp, port="http,https"]
sendmail[name=api, [email protected], [email protected]]
logpath = /var/log/httpd/*access_log
[zulu]
enabled = true
filter = zulu
action = iptables-allports[name=zulu, protocol=tcp]
sendmail[name=zulu, [email protected], [email protected]]
logpath = /var/log/asterisk/zulu_out.log
[openvpn]
enabled = true
filter = openvpn
action = iptables-multiport[name=openvpn, protocol=udp, port=1220]
sendmail[name=openvpn, [email protected], [email protected]]
logpath = /var/log/openvpn.log
[recidive]
# recidivist.
#
# Noun: A convicted criminal who reoffends, especially repeatedly.
#
enabled = true
filter = recidive
logpath = /var/log/fail2ban.log*
action = iptables-allports[name=recidive, protocol=all]
sendmail[name=recidive, [email protected], [email protected]]
bantime = 604800 ; 1 week
findtime = 86400 ; 1 day
maxretry = 20