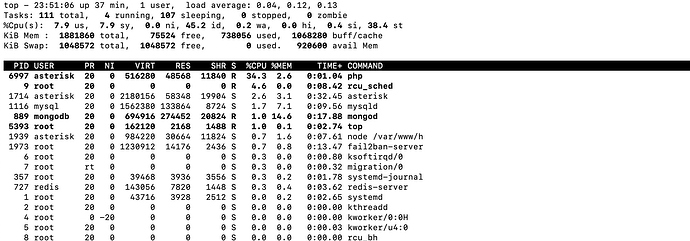
Hi, thanks for the reply! Yeah, I can catch it consistently with both and I have some audio breakup when it runs.
When I ran that it completed in less than a second. Here is the output:
[root@pbx ~]# /sbin/runuser asterisk -c /var/www/html/admin/modules/firewall/bin/getservices
{“smartports”:{“signalling”:{“udp”:[{“dest”:“::”,“dport”:5160,“name”:“chansip”},{“dest”:“::”,“dport”:“5060”,“name”:“pjsip”}],“tcp”:},“rtp”:{“start”:10000,“end”:20000},“udptl”:{“start”:4000,“end”:4999},“known”:[“64.2.142.190”,“64.2.142.188”,“64.2.142.17”,“64.2.142.111”,“64.2.142.107”,“64.2.142.189”,“64.2.142.215”,“64.2.142.216”,“64.2.142.187”,“64.2.142.106”,“64.2.142.109”,“66.241.99.22”],“registrations”:[“66.241.99.22”,“64.2.142.190”]},“settings”:{“ssf”:true,“period”:60,“responsive”:true,“rprotocols”:{“pjsip”:{“state”:“1”,“descr”:“SIP Protocol (pjsip)”},“chansip”:{“state”:“1”,“descr”:“Legacy SIP (chan_sip)”},“iax”:{“state”:false,“descr”:“IAX Protocol”}}},“blacklist”:,“fw”:{“ssh”:[{“protocol”:“tcp”,“port”:22}],“http”:[{“protocol”:“tcp”,“port”:“80”,“leport”:true}],“https”:[{“protocol”:“tcp”,“port”:443}],“ucp”:,“pjsip”:[{“protocol”:“udp”,“port”:“5060”}],“chansip”:[{“protocol”:“udp”,“port”:5160}],“iax”:[{“protocol”:“udp”,“port”:4569}],“webrtc”:[{“protocol”:“tcp”,“port”:8088},{“protocol”:“tcp”,“port”:8089}],“letsencrypt”:,“zulu”:,“isymphony”:,“provis”:[{“protocol”:“tcp”,“port”:“84”,“ratelimit”:true,“leport”:true}],“provis_ssl”:,“vpn”:[{“protocol”:“udp”,“port”:1194}],“restapps”:[{“protocol”:“tcp”,“port”:“82”,“leport”:true}],“restapps_ssl”:,“xmpp”:[{“protocol”:“tcp”,“port”:5222}],“ftp”:[{“protocol”:“tcp”,“port”:21}],“tftp”:[{“protocol”:“udp”,“port”:69}],“nfs”:,“smb”:},“services”:{“ssh”:{“name”:“SSH”,“defzones”:[“internal”],“descr”:“SSH is the most commonly used system administration tool. It is also a common target for hackers. We <strong>strongly recommend</strong> using a strong password and SSH keys. “,“fw”:[{“protocol”:“tcp”,“port”:22}],“noreject”:true,“guess”:“Warning: Unable to read /etc/ssh/sshd_config - this port may be incorrect. This is <strong>expected</strong> when viewing through the Web Interface. The correct port, as configured, will be used in the firewall service.”,“zones”:[“internal”]},“http”:{“name”:“Web Management”,“defzones”:[“internal”],“descr”:“Web management interface for your PBX. This is the http, not https (secure) interface.”,“fw”:[{“protocol”:“tcp”,“port”:“80”,“leport”:true}],“zones”:[“internal”]},“https”:{“name”:“Web Management (Secure)”,“defzones”:[“internal”],“descr”:“Web management interface for your PBX. This is the https interface.”,“fw”:[{“protocol”:“tcp”,“port”:443}],“noreject”:true,“zones”:[“internal”]},“ucp”:{“name”:“UCP”,“defzones”:[“external”,“other”,“internal”],“descr”:“Dedicated UCP access is disabled in Sysadmin Port Management”,“fw”:,“disabled”:true,“zones”:[“external”,“other”,“internal”]},“pjsip”:{“name”:“SIP Protocol”,“defzones”:[“other”,“internal”],“descr”:“This is the SIP driver (pjsip). Most devices use SIP.<div class=‘well’>This protocol is being managed by the Responsive Firewall. You <strong>should not</strong> enable access from the ‘Internet’ zone, or Responsive Firewall will be bypassed.</div>”,“fw”:[{“protocol”:“udp”,“port”:“5060”}],“zones”:[“internal”]},“chansip”:{“name”:“CHAN_SIP Protocol”,“defzones”:[“internal”],“descr”:“This is the legacy chan_sip driver.<div class=‘well’>This protocol is being managed by the Responsive Firewall. You <strong>should not</strong> enable access from the ‘Internet’ zone, or Responsive Firewall will be bypassed.</div>”,“fw”:[{“protocol”:“udp”,“port”:5160}],“zones”:[“internal”]},“iax”:{“name”:“IAX Protocol”,“defzones”:[“internal”],“descr”:“IAX stands for Inter Asterisk eXchange. It is more bandwidth efficient than SIP, but few providers support it.”,“fw”:[{“protocol”:“udp”,“port”:4569}],“zones”:[“internal”]},“webrtc”:{“name”:“WebRTC”,“defzones”:[“internal”],“descr”:“WebRTC is used by UCP (and other services) to enable calls to be made via a web browser.”,“fw”:[{“protocol”:“tcp”,“port”:8088},{“protocol”:“tcp”,“port”:8089}],“zones”:[“internal”]},“letsencrypt”:{“name”:“LetsEncrypt”,“descr”:“This will allow access to the LetsEncrypt service when it is enabled.”,“fw”:,“defzones”:,“disabled”:true,“zones”:},“zulu”:{“name”:“Zulu UC”,“defzones”:[“external”,“other”,“internal”],“descr”:“Zulu is not not available on this machine”,“disabled”:true,“fw”:,“zones”:[“external”,“other”,“internal”]},“isymphony”:{“name”:“iSymphony”,“defzones”:[“internal”],“descr”:“iSymphony is not installed on this server.”,“disabled”:true,“fw”:,“zones”:[“internal”]},“provis”:{“name”:“HTTP Provisioning”,“defzones”:[“other”,“internal”],“descr”:“Phones that are configured via Endpoint Manager to use HTTP provisioning will use this port to download its configuration. It is NOT ADVISED to expose this port to the public internet, as SIP Secrets will be available to a knowledgable attacker.”,“fw”:[{“protocol”:“tcp”,“port”:“84”,“ratelimit”:true,“leport”:true}],“zones”:[“other”,“internal”]},“provis_ssl”:{“name”:“HTTPS Provisioning”,“defzones”:[“other”,“internal”],“descr”:“HTTPS Provisioning is disabled in Sysadmin Port Management”,“fw”:,“disabled”:true,“zones”:[“other”,“internal”]},“vpn”:{“name”:“OpenVPN Server”,“defzones”:[“external”,“other”,“internal”],“descr”:“This allows clients to connect to an OpenVPN server running on this machine. This is an inherently secure protocol.”,“fw”:[{“protocol”:“udp”,“port”:1194}],“zones”:[“external”,“other”,“internal”]},“restapps”:{“name”:“REST Apps (HTTP)”,“defzones”:[“internal”],“descr”:“REST Apps are used with intelligent phones to provide an interactive interface from the phone itself. Note that any devices that are allowed access via Responsive Firewall are automatically granted access to this service.”,“fw”:[{“protocol”:“tcp”,“port”:“82”,“leport”:true}],“zones”:[“internal”]},“restapps_ssl”:{“name”:“REST Apps (HTTPS)”,“defzones”:[“internal”],“descr”:“HTTPS REST Apps are disabled in Sysadmin Port Management”,“fw”:,“disabled”:true,“zones”:[“internal”]},“xmpp”:{“name”:“XMPP”,“defzones”:[“external”,“other”,“internal”],“descr”:“This is the XMPP server. If you wish to connect to it using an external Jabber client, you need to open this port.”,“fw”:[{“protocol”:“tcp”,“port”:5222}],“zones”:[“external”,“other”,“internal”]},“ftp”:{“name”:“FTP”,“defzones”:[“internal”],“descr”:“FTP is used by Endpoint Manager to send firmware images to phones, as well as additional data.”,“fw”:[{“protocol”:“tcp”,“port”:21}],“zones”:[“internal”]},“tftp”:{“name”:“TFTP”,“defzones”:[“internal”],“descr”:“TFTP is used normally for provisioning and upgrading of devices.”,“fw”:[{“protocol”:“udp”,“port”:69}],“zones”:[“internal”]},“nfs”:{“name”:“NFS”,“defzones”:[“reject”],“fw”:,“descr”:“NFS Services are not available on this machine”,“disabled”:true,“zones”:[“reject”]},“smb”:{“name”:“SMB/CIFS”,“defzones”:[“reject”],“fw”:,“descr”:“SMB/CIFS (Samba) is not installed on this machine”,“disabled”:true,“zones”:[“reject”]}},“custom”:,“hostmaps”:{“127.0.0.1”:“trusted”,”::1”:“trusted”,“38.22.6.101”:“trusted”},“safemode”:{“status”:“enabled”,“lastuptime”:59959},“advancedsettings”:{“safemode”:“enabled”,“masq”:“enabled”,“lefilter”:“enabled”,“customrules”:“disabled”,“rejectpackets”:“disabled”},“fwversion”:“15.0.6.34”}