I was trying out this firewall feature in FreePBX13 and when I moved the FreePBX server Ethernet connection to the external zone I was locked out of the GUI. This even though I put the IP of the computer connecting from in the “trusted” computers list. How Can I disable the firewall from the cli at the PBX server so I can get back the FreePBX GUI? I can’t find the CLI list of commands for the firewall anywhere on the forum or in the documentation.
I had the same thin happen. i uninstalled the firewall module via the following code.
amportal a ma uninstall firewall
the only issue I am running into is when I reinstall the firewall and enable it lock me out before I can make changes. Does anyone know what files I need to delete to remove the configuration?
You can, by default, access the https:// connection of your machine, which will let you fix the configuration. You’ll get a certificate error, but you should still be able to get in.
Hi Rob,
I had the firewall setup nicely with my hosted PBX, but then I did the update and lost all my settings. Now my extensions only register if I’m connecting from a trusted IP. The responsive firewall does not seem to be working correctly.
Also, it appears the firewall settings are lost every time asterisk is restarted. I believe this is a safety feature but…I think this needs to be a feature that can be turned off.
D Rubie
Hrm, well, yes, I guess that’s SORT of true. Responsive firewall quizzes Asterisk for its registrations. If asterisk is restarted, those phones won’t be registered, so they won’t be visible.
However, the phones should automatically reregister, and reappear. Is that not what’s happening?
If you’re saying that EVERYTHING breaks, then that’s wrong and terrible, and is a bug and you should be yelling at me about it 8)
The last update (13.0.6) fixed all the issues I was having…the most important being the ability for remote registrations.
Thanks
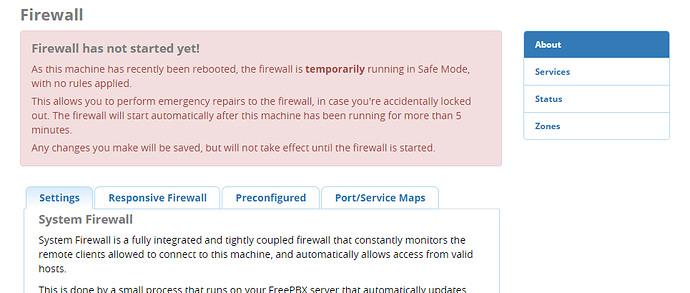
I’ve been having a think about this, and I’ve decided that the firewall will not be active until the machine has been up for more than 5 minutes…
The last thing I want is for people to be inadvertently locked out of their machines without any ability to get back in, so I’m going to add a little timeout, so that if something DOES go terribly wrong, you can reboot the machine, and then get in and fix it before it locks you out.
I’ll have a go at doing that today.
Conversely, Perhaps the Firewall should be up for five minutes to prove it’s solidity, if you can’t log, or it goes to shi! for your clients, in for those five minutes . . . . then it turns itself off so you can fix the broken bits, no? (kinda like csf  ) when it is all absolutely working perfectly , say ok to something , or let incron do that for you.
) when it is all absolutely working perfectly , say ok to something , or let incron do that for you.
That means that you’ll need to log into your machine every time it’s rebooted, before the firewall is activated.
No, that means if the firewall doesn’t work, then five minutes later it will turn itself off, “so you can fix it” When it works , give it your imprimatur . It’s hard to reboot a machine you don’t have access to.
Oh, you’re saying a rollback.
Yes, I’ve been looking into that. There’s actually a bit of code already there to handle it, look for ‘canRevert’. I’ll use shared memory and IPC to handle it, but that’s going to be a fair way down the track.
Rollback, cover your ass, whatever, it is a good thing  .
.
Personally , most of my machines are now virtualized so not a prob, the few on-site ones still have /dev/tty? backup access on their telco alarm lines, just for really bad days, if neither were available then an overly restrictive iptables rule would be a bad thing, maybe portknocker in the interim .
Exactly the reason for the 5 minute delay.
perhaps I’m missing something, in your scenario, for the first five minutes, the firewall is off, no?
So when it turns on and you got it wrong, what happens ? . . . . .
The firewall is always on. If you make some catastrophic mistake like blacklisting your entire network, then you reboot the machine, log in, fix it, and that’s it.
Ok, now I am confused, where is my confusion as to your two previous statements
“I’ve decided that the firewall will not be active until the machine has been up for more than 5 minutes"
and later
"The firewall is always on”
but if some situation where you ". . . make some catastrophic mistake like blacklisting your entire network . . . " how will you just “. . . reboot the machine, log in, fix it, and that’s it” ?
Yep, that’s a good summary.
But because you have now blacklisted the entire network, how can you now remotely “. . .reboot the machine, log in, fix it, and that’s it” ?
( p.s. And after rereading , I would respectfully state that my post was not a summary , it was in fact a question.)
Um, I don’t know? That’s kinda up to the implementer. At worst, you would call someone and say ‘Can you please push the reset button on machine XYZ’.
You were asking ‘what happens when you turn the firewall on after giving it a bad config’. That’s not how the firewall works. It’s on all the time.